Cybersecurity has been a hot topic for years. With many high-profile breaches, malware attacks, and pricey payouts, it’s no wonder why companies continue to add more and more protection for their IT systems.
Despite this, hackers continue to succeed at exploiting vulnerabilities. Why are there still vulnerabilities in the first place? All it takes is one weak spot and one bad actor (looking at you, HAL 9000) to lock you out and leave you scrambling to regain control.
In this post, we’ll cover how network infrastructure has evolved in the past decade, why cybersecurity can make you feel lost in space, and why recovery is crucial to modern cybersecurity.
How network infrastructure evolved
The movie 2001: A Space Odyssey predicted that by the year 2001, technological advancements would enable things like space travel and virtual conferencing. In reality, we were still rolling around in gas-powered cars or waiting for 56kbps dial-up connections to load our email inboxes.
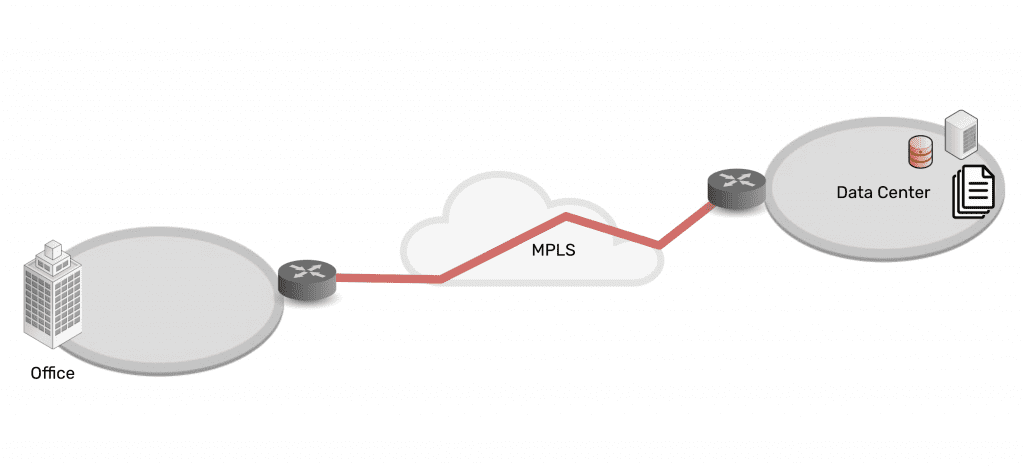
Times were simpler, but that also meant that network infrastructure and cybersecurity were simpler. Most people would go to work at a physical location like an HQ or branch office, and distributed or remote work technologies were very much in their infancy. This meant that network infrastructures were more simple and localized, usually requiring a simple MPLS connection from their off-site data center (if they had one) to their branch offices. Cybersecurity was simple: it was either inherent to the connection type (like MPLS), or required something like a basic firewall or encryption method.
Fast forward more than 20 years, and the network infrastructure common to 2001 is barely recognizable. With customers and employees demanding companies adapt to their on-the-go and remote-work lifestyles, the network infrastructure exploded, causing a sort of Big Bang of cybersecurity as we know it today.
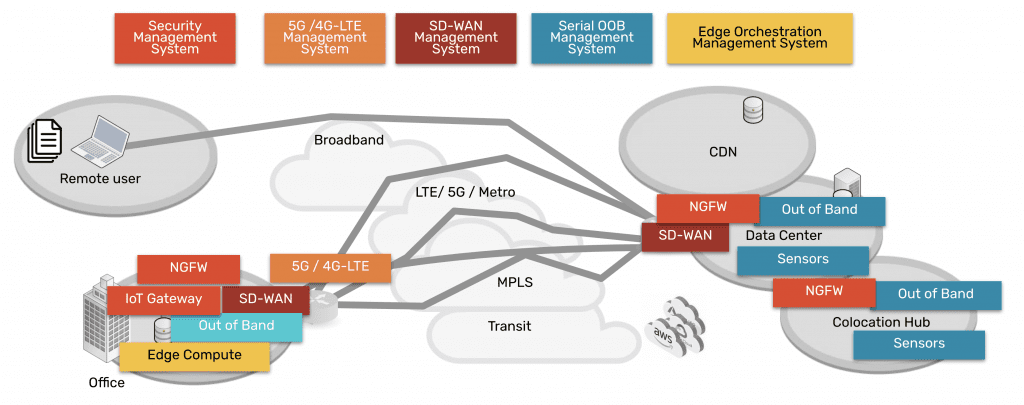
Modern networks need to serve many branch offices and remote locations, and the only way to succeed is by incorporating a myriad of on-prem, cloud, and SaaS solutions. This creates a hybrid infrastructure of data, security, networking, and computing distributed everywhere. In other words, the attack surface continues to expand much like the universe itself, and security professionals have been struggling to contain all the vulnerabilities left in its wake.
Why cybersecurity makes you feel lost in space
You might relate to Frank Poole. In the movie, the HAL 9000 supercomputer leads Frank to perform a spacewalk in order to repair a portion of their ship. While Frank floats toward the ship, the corrupted HAL takes control of an EVA pod and slams it into Frank, causing him to tumble helplessly through the black void of space and eventually meet his demise.
Trying to secure your IT infrastructure can make you feel just as helpless and out of control. That’s because cybersecurity presents several challenges that make it difficult to gain your footing. And with 2021’s executive order regarding zero trust security, cybersecurity seems even more daunting as previous protection methodologies are becoming wholly obsolete.
Here’s a brief look at some of the challenges of modern cybersecurity.
Too many products
Regardless of your industry, there are so many security products to choose from that it can easily feel like you’re floating amongst an endless sky of stars. It’s difficult enough choosing properly secured servers, routers, storage devices, and other physical equipment. Add on the other crucial pieces of the modern network architecture, and it’s easy to make a full time job of researching, comparing, and selecting the right cloud and SaaS security products. Here’s a list that barely scratches the surface of different types of security products to choose from:
- Firewalls & next-gen firewalls (NGFWs)
- Security information and event management (SIEM) systems
- Identify and access management (IAM) products
- Pen testers
- Data analytics
- Intrusion prevention and detection systems (IDPS)
- Endpoint protection apps
- Database security solutions
- Ransomware/malware detection and removal
- Authentication and single sign-on
Too many vendors
All of these products have to originate from somewhere, which brings us to the next challenge: there are too many cybersecurity vendors to choose from. This isn’t necessarily a bad thing, since competition creates better products, but it does complicate the cybersecurity professional’s journey to achieving holistic protection.
At RSA Conference 2022, for example, there were 450 security exhibitors present, 70 of which were funded well enough to afford the cost of a booth. During the show, many discussed that in the previous 18 months there were 1,800 new cybersecurity vendors that received funding to be installed in networks. The TL;DR — this multi-vendor ecosystem will persist (and probably grow even more), and so will the challenge of achieving holistic security.
Of course everyone wants the best of the best, which might draw your attention to staples like Cisco, Fortinet, and Palo Alto Networks. But because the modern hybrid infrastructure is so diverse, there now exist so many niche products available from thousands of vendors. In fact, CyberDB compiled a database that includes more than 3,500 security companies from the United States alone.
Here’s a graphic that puts into perspective just a fraction of the available vendors:
Too many gaps
The third and most important challenge stems from the first two above: there are just too many security gaps to address. Part of this problem is due to the diversity of hybrid infrastructure. But once you’re able to identify the gaps, you’ll find that addressing these will more often than not create even more gaps.
That’s because there’s no single vendor or suite of products that provides holistic cybersecurity. You deploy a variety of products but inevitably run into interoperability issues, which only perpetuates more vulnerabilities as you add more solutions to address these gaps.
What you end up with is a plethora of solutions that are secure themselves, but that don’t provide protection for your infrastructure as a whole.
Why recovery is key to modern cybersecurity
According to a Sophos survey, 66% of surveyed organizations suffered ransomware attacks in 2022. And when attacks happened, 70% of organizations needed more than two weeks to recover. Ransomware is the modern disaster, which makes minimizing recovery times an essential part of modern cybersecurity.
Recall the Fortinet 7.0 CVE from 2022. Customers upgrading to the then latest release of FortiOS suddenly found themselves vulnerable to an authentication bypass, where attackers could gain admin access using certain HTTP/S requests. This typical scenario leaves IT teams waiting for a solution while their business remains vulnerable. What’s needed is the ability to recover quickly and automatically, whether from an active attack or an at-risk configuration.
Get the blueprint for fast recovery times
Big Tech companies have spent years building this capability into their infrastructure. At ZPE Systems, we’ve directly collaborated with these companies and have created best practices based on these proven architectures. This Network Automation Blueprint details the components and practical steps to take, from automating IT/OT production infrastructure, to implementing an effective design for orchestration and automation environments.
The blueprint is your template to achieving fast recovery times and reducing your risk of attack. Download the blueprint now.
Watch the blueprint recover a failed upgrade
Watch this tech demo from Tech Field Day 26, where Rene Neumann shows how the blueprint helps you recover a failed device upgrade in minutes.