Blogs / Vlogs

Cisco 4351 EOL Replacement Guide
This guide compares Cisco 4351 EOL replacement options and discusses the innovative features and capabilities offered by Gen 3 branch networking solutions.

Opengear Alternatives for the OM2200 and OM1200
This blog reviews the Operations Manager platform before discussing Opengear alternatives that provide greater automation, security, and branch networking capabilities.

SD-WAN Leaders Analysis Report
This report uses Gartner’s Magic Quadrant and independent analysis to compare the six SD-WAN leaders based on key factors like features and versatility.

Opengear ACM7000 Resilience Gateway Alternative Options
Discussing the Opengear ACM7000 Resilience Gateway and its limitations as well as alternative options from ZPE Systems that cover these gaps for greater resilience and control.

Network Resilience vs Redundancy vs Backups
This article compares network resilience vs. redundancy and backups and describes some of the tools and best practices for ensuring resilience.

The Future of Edge Computing
Discussing the future of edge computing as described by leading analysts at Gartner, which relies on comprehensive strategies and centralized, vendor-neutral edge management and orchestration.
Distributed Edge Computing Use Cases
This post discusses six distributed edge computing use cases, including healthcare, finance, oil & gas, manufacturing, utilities/public services, and AI & machine learning.

DORA Act: 5 Takeaways For The Financial Sector
The Digital Operational Resilience Act (DORA Act) outlines significant resilience changes for the financial sector. See how to comply here.
Edge Computing Ecosystem Design
This post discusses the challenges created by a fragmented edge computing market before providing edge computing ecosystem design best practices to overcome these hurdles.

Zero Trust Edge Solutions: Continuing the Zero Trust Journey
This guide explains what zero trust edge solutions do and the challenges involved in using them before discussing how to build a unified ZTE platform.

What to do if You’re Ransomware’d: A Healthcare Example
Cybersecurity expert James Cabe discusses what to do if you’re on the receiving end of a ransomware attack, including isolating systems.
IT Automation vs Orchestration: What’s the Difference?
This guide compares IT automation vs orchestration to clear up misconceptions and help you choose the right approach to streamlining your IT operations.
Edge Computing vs On-Premises: A Comparison
This guide defines edge computing vs on-premises computing in detail before analyzing the advantages and challenges involved with each approach.

Zero Trust Security Benefits
Discussing how zero trust security benefits organizations by increasing visibility, reducing the attack radius, and providing precise security coverage.

Network Management Best Practices
This guide discusses the network management best practices for improving and supporting network resilience.

Network Resilience: What is a Resilience System?
This guide to network resilience defines resilience systems, discusses use cases and related technologies, and describes the key components required to build them.

Out-of-Band Management: What It Is and Why You Need It
This guide to out-of-band management answers critical questions about what this technology is, why you need it, and how to choose the right solution.
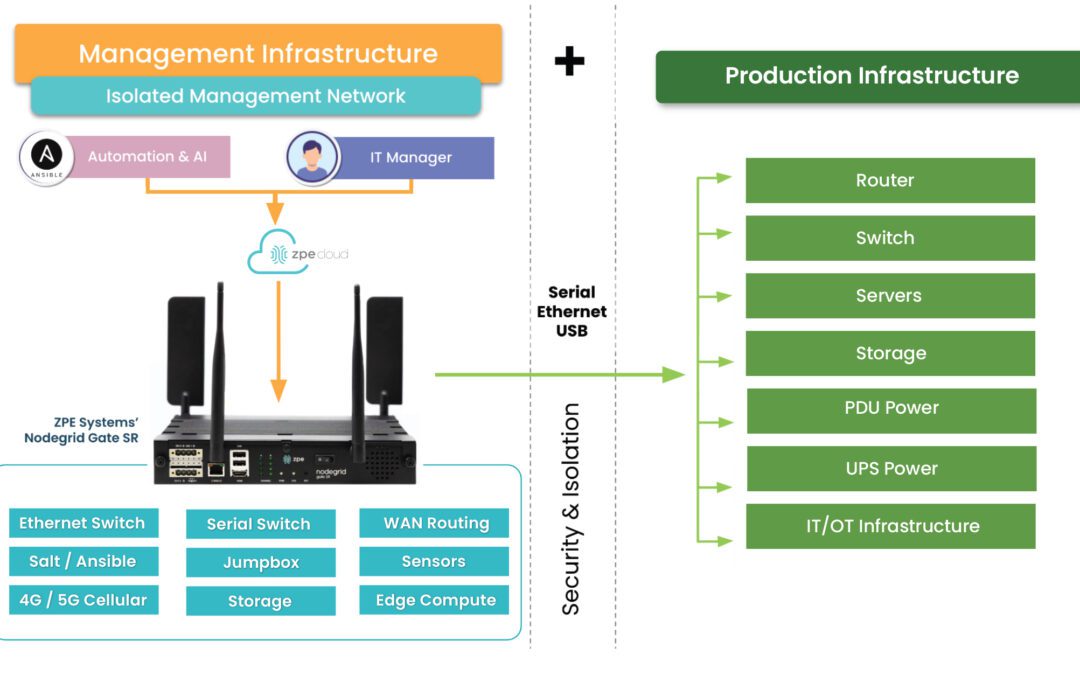
Why network resilience requires Isolated Management Infrastructure
Isolated Management Infrastructure is the key to modern network resilience. Read about the gaps of existing approaches and why Big Tech trusts IMI.

Network Resilience Doesn’t Mean What it Did 20 Years Ago
Network resilience requirements have changed. James Cabe discusses why the new standard is Isolated Management Infrastructure.

Edge Computing Requirements
This guide discusses the edge computing requirements for hardware, networking, availability, security, and visibility to ensure a successful deployment.

IT Infrastructure Management Best Practices
This guide discusses IT infrastructure management best practices for creating and maintaining more resilient enterprise networks.

Legrand Acquires ZPE Systems, Inc.
ZPE Systems is now a brand of Legrand! Read the full press release for details about the acquisition.
Collaboration in DevOps: Strategies and Best Practices
This guide to collaboration in DevOps provides tips and best practices to bring Dev and Ops together while minimizing friction for maximum operational efficiency.

Terminal Servers: Uses, Benefits, and Examples
This guide answers all your questions about terminal servers, discussing their uses and benefits before describing what to look for in the best terminal server solution.
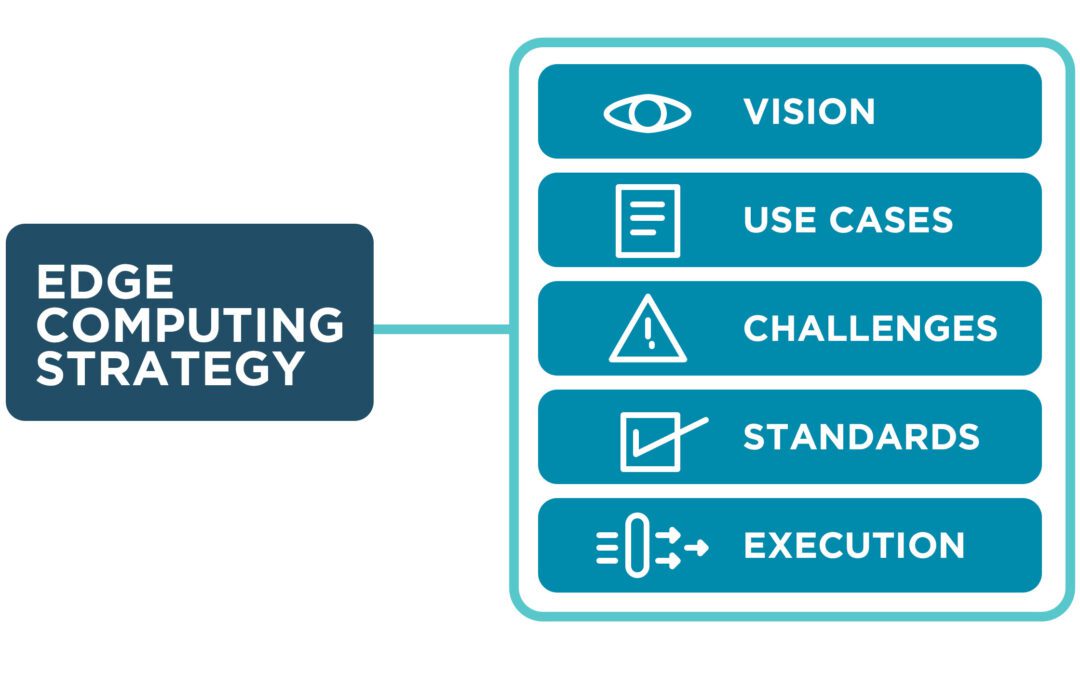
Gartner Market Guide for Edge Computing
Discussing the Gartner Market Guide for Edge Computing and their recommendations for building a strategy to manage and orchestrate your edge solutions.

What is a Hyperscale Data Center?
This blog defines a hyperscale data center deployment before discussing the unique challenges involved in managing and supporting such an architecture.

Healthcare Network Design
A guide to resilient healthcare network design using technologies like automation, edge computing, and isolated recovery environments (IREs).

Legrand Intends to Acquire ZPE Systems
Legrand, a global powerhouse for hyperscale data centers, enriches its offerings by acquiring ZPE Systems resilience platform.

Best DevOps Tools
This blog discusses the various workflows involved in the DevOps lifecycle that can be automated with the best DevOps tools.

Best Network Performance Monitoring Tools
This guide compares three of the best network performance monitoring tools by analyzing the most critical factors and discussing the pros and cons.

Breaking Down The 2023 Ragnar Locker Cyberattacks
Many organizations suffered Ragnar Locker cyberattacks in 2023. 30-year cybersecurity expert James Cabe discusses the problem and solution.

Nodegrid OS and ZPE Cloud achieve industry’s highest security with Synopsys
ZPE Systems achieves the industry’s highest security level by incorporating Synopsys code-quality measures. Read the details here.

OOB Network Management Software Tools
Comparing the four best OOB network management software tools and discussing the features, pros, and cons to help you make the best choice for your environment.

Living Spaces Furniture: Scaling to 50 sites with only 3 network staff
Download the case study to see how Living Spaces cut costs by $300,000 per year and scaled across the U.S. with only 3 network staff.

ISP Network Architecture
Explaining the challenges that make ISP network architectures less resilient and providing solutions for overcoming these hurdles.

Multi-Organization Access For ZPE Cloud, Ideal for Managed Service Providers
ZPE Cloud now features seamless, multi-organization access that is ideal for Managed Service Providers.

Isolated Management Infrastructure & Security with Nodegrid OS v5.10
ZPE Systems’ Nodegrid provides the Isolated Management Infrastructure that allows IT teams to quickly recover from outages and ransomware.

Edge Management and Orchestration
This post summarizes Gartner’s advice for building an edge computing strategy and discusses how an edge management and orchestration solution like Nodegrid can help.

Dissecting the MGM Cyberattack: Lions, Tigers, & Bears, Oh My!
Casino giants in the US were hit by ransomware in September 2023. Cyber expert James Cabe breaks down the attack & how to recover.

Intel NUC Use Cases
This post describes some of the most common Intel NUC use cases, explains the security and management issues that caused its discontinuation, and provides superior replacement options.

What is Zero Trust Security?
What is zero trust security? This post defines the term and discusses its history before providing a guide to implementing zero trust in your organization.

IT Infrastructure Management Challenges
This post analyzes the top 5 IT infrastructure management challenges while providing potential solutions and additional resources.

What is a radio access network (RAN)?
This post provides an introduction to radio access networks (RAN) before discussing 5G RAN challenges, solutions, and use cases.

Data Center Migration Checklist
This data center migration checklist will help guide your planning and ensure you’re asking the right questions and preparing for any potential problems.

Operational Technology Security
This guide defines OT, explains how to overcome some of the biggest operational technology security challenges, and discusses the importance of recovery in building resilience in OT.
Medical Devices Cybersecurity Risk
Discussing the factors that make medical devices a cybersecurity risk before providing mitigation strategies to help healthcare organizations.

Zero Trust Security Architecture
This post defines a zero trust security architecture, discusses some of the gaps typically left in such an architecture, and provides tips for avoiding these pitfalls.

SSE Magic Quadrant: Key Takeaways of the 2023 Report
Gartner’s SSE Magic Quadrant for 2023 identifies 10 key vendors currently providing secure service edge capabilities for the enterprise market. In this guide, we’ll summarize the common factors...

What is an Application Delivery Platform?
This guide defines an application delivery platform, discusses the underlying technology, and highlights a leading platform engineering solution.
Carrier Community Enterprise 2023 – Berlin
ZPE Systems’ Rene Neumann is joined by other panelists in Carrier Community.

The Biggest Ransomware Attack You Haven’t Heard of…Yet
The most successful ransomware attack ever is happening right now. See why isolated management infrastructure is the only way to save your organization.
Best Practices to Protect your Infrastructure & Combat Ransomware with ZPE Systems Services Delivery Platform
Koroush Saraf shows why cyberattacks are still successful despite thousands of security products, and the best practice to stop attacks.

How to Implement Zero Trust for OT
Zero trust for OT uses network segmentation, strong security policies, and advanced security technologies to protect operational technology from attack.

SD-WAN ROI Calculator & Cost Reduction Strategies
A discussion of how SD-WAN decreases branch networking costs, including an SD-WAN ROI calculator for a more personalized estimate of the potential savings.

IoT in Finance Industry and Security Challenges
This post discusses how to take advantage of IoT in the finance industry by overcoming security challenges with automation, secure platforms, and vendor-neutral orchestration.

Atsign: Why Choose ZPE Systems to Host IoT Security?
In this guest post, Atsign CTO & Co-Founder Colin Constable discusses how their IoT security solutions just work with ZPE Systems.

Opengear EOL: IM7200 Alternative Options
The Opengear Infrastructure Manager has a great reputation, but there are some alternatives to explore as well. This post dives into the benefits of the IM7200 as well as worthwhile alternatives.
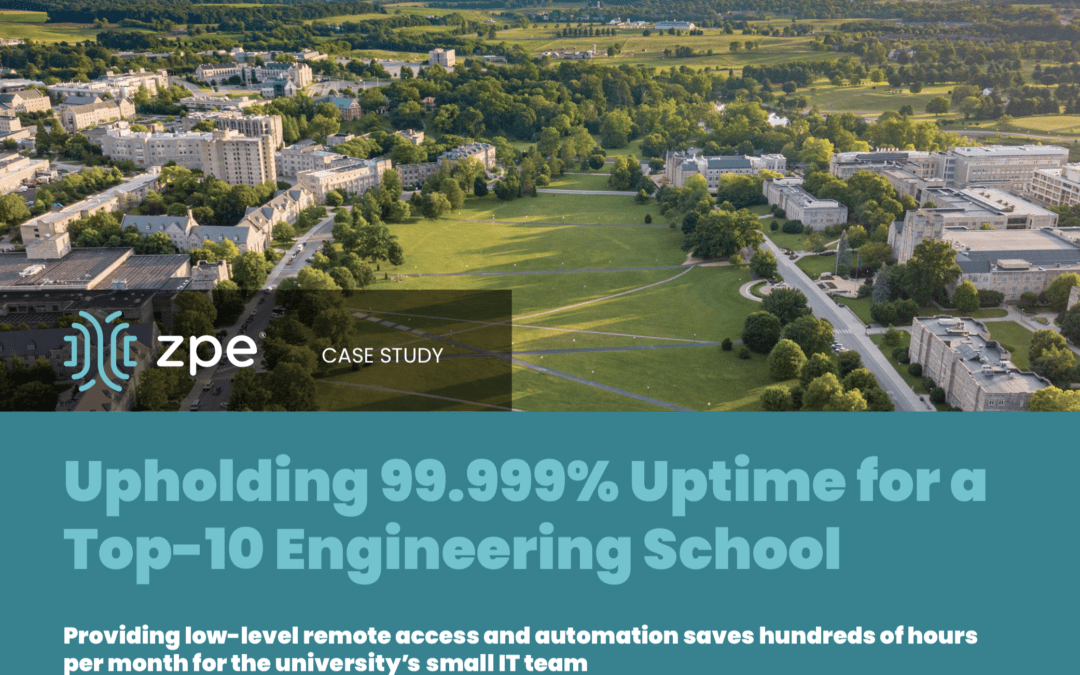
99.999% Uptime for a Top-10 Engineering School
From data center to edge, see how Nodegrid Services Routers saved hundreds of hours per month for an engineering school’s IT team.

Network Automation Cost Savings Calculator
This post discusses how to save money through automation and provides a network automation cost savings calculator for a more customized estimate of your potential ROI.
Best Intel NUC Alternatives
Discussing the challenges and security risks associated with Intel NUC jump boxes before providing enterprise-grade Intel NUC alternatives that solve these problems.

Cisco 2900 EOL: Replacement Options
In this guide, we’ll compare migration options for the Cisco ISR 2900 EOL models to help you select a solution that suits your business use case, deployment size, and future growth.
Raspberry Pi Alternatives for Business
The Nodegrid line of Raspberry Pi alternatives from ZPE Systems can help your organization prevent Shadow IT to reduce your attack surface and improve your security posture without increasing costs.
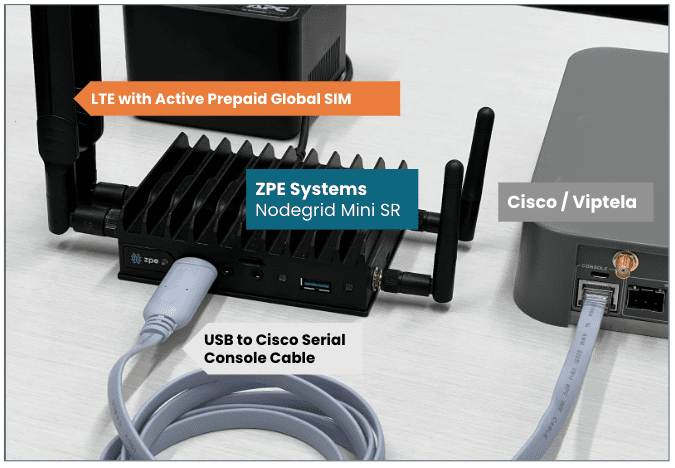
Defusing Cisco SD-WAN Time-bomb requires out-of-band access
Viptela SD-WAN devices are used at large enterprise branches all around the world. The success of SD-WAN replaced dedicated service provider managed MPLS with customer managed boxes that used...
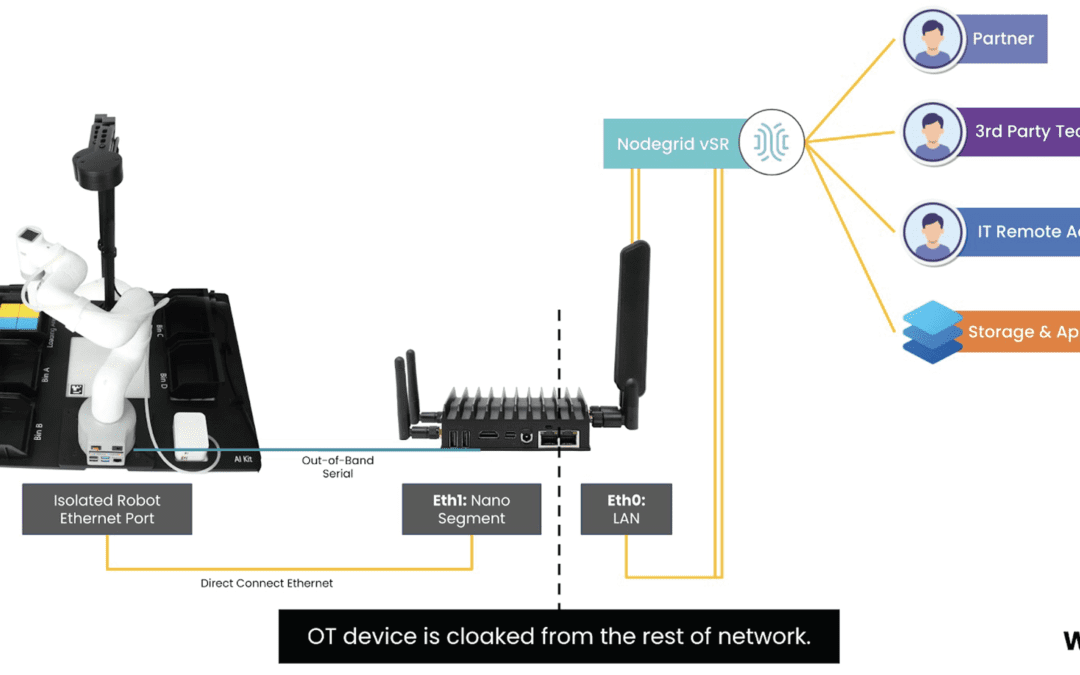
How to remove IoT & OT from your attack surface
Summary With IoT and OT (operationalized technology) sprawling across the globe, organizations are able to provide more value to their customers. But for IT security teams, this presents a growing...

Edge Pen Testing: Run Horizon3 on ZPE Systems’ Services Delivery Platform
Summary Enterprise IT teams struggle to secure their environments. One proven approach is for teams to attack their own network, a process called security penetration testing, which is executed...

SASE: Deliver Cloudflare anywhere with ZPE Systems’ Services Delivery Platform
Summary Cloudflare One provides Secure Access Service Edge (SASE) and Zero Trust Network Access (ZTNA). This industry-leading solution is trusted worldwide to provide enterprises with secure...
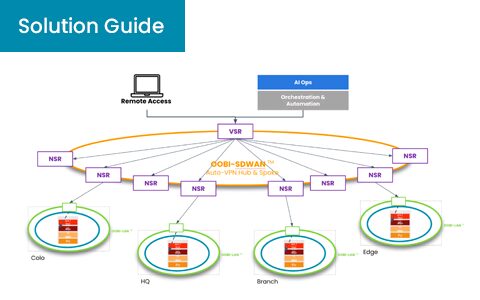
ZPE Systems’ Nodegrid Virtual Services Router (VSR) and Out-of-Band Infrastructure WAN (OOBI-WAN)
Summary Most enterprises operate a hybrid- or multi-cloud environment, which adds significant overhead, complexity, and architectural challenges. This turns networking and security into an...
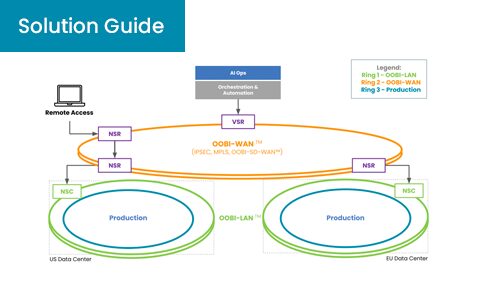
Automated Infrastructure Patching for Ransomware Defense
Summary Ransomware attacks continue to be successful because organizations often leave infrastructure unpatched. IT teams sit on the latest patches and updates from their solution vendors, which...
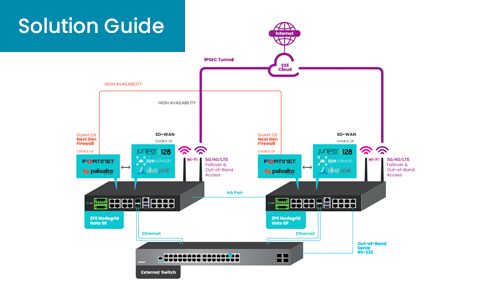
ZPE Systems’ Services Delivery Platform: Deploy Any App, Any Time, Anywhere
Summary Organizations struggle to manage the hundreds of products involved in enterprise security. Most NGFWs, SD-WAN, pen testers, and on-prem & cloud solutions require hardware platforms to be...

What is Security as a Service?
Defining Security as a Service, discussing the pros and cons, and describing an alternative solution for streamlined and scalable cybersecurity management.

Enterprise Network Management Trends to Expect in 2023 and Beyond
Discussing the network management trends observed among enterprises trying to address the unique challenges faced by network teams in 2023 and beyond.
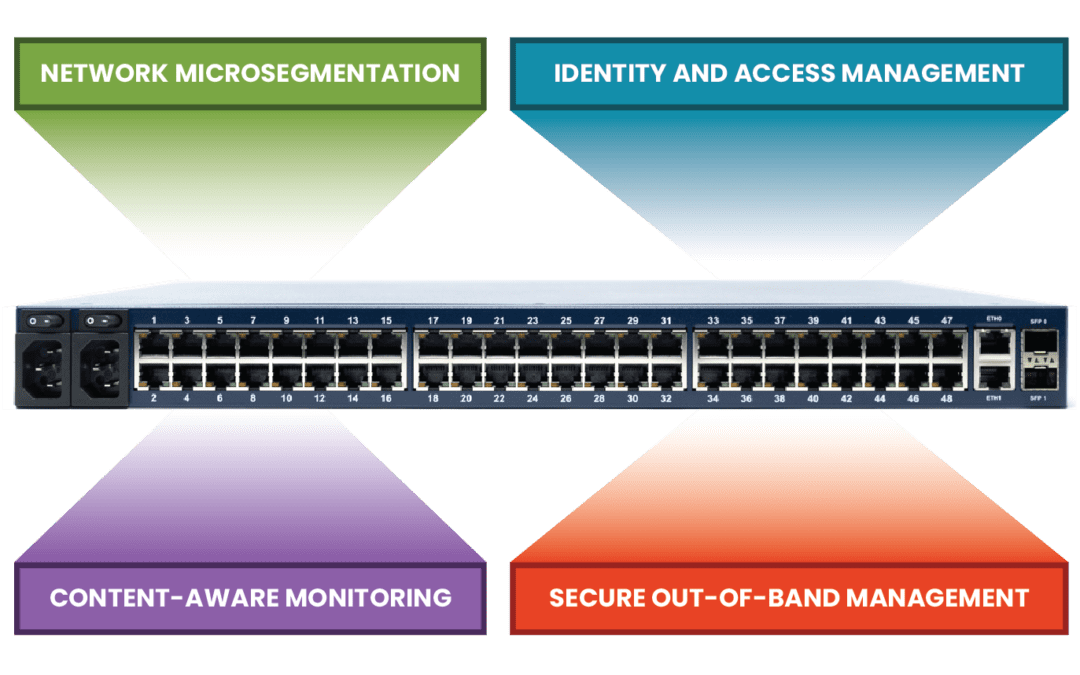
What Is a Zero Trust Gateway?
This post discusses the technologies that make up a zero trust gateway and explains how they work together to defend enterprise networks.
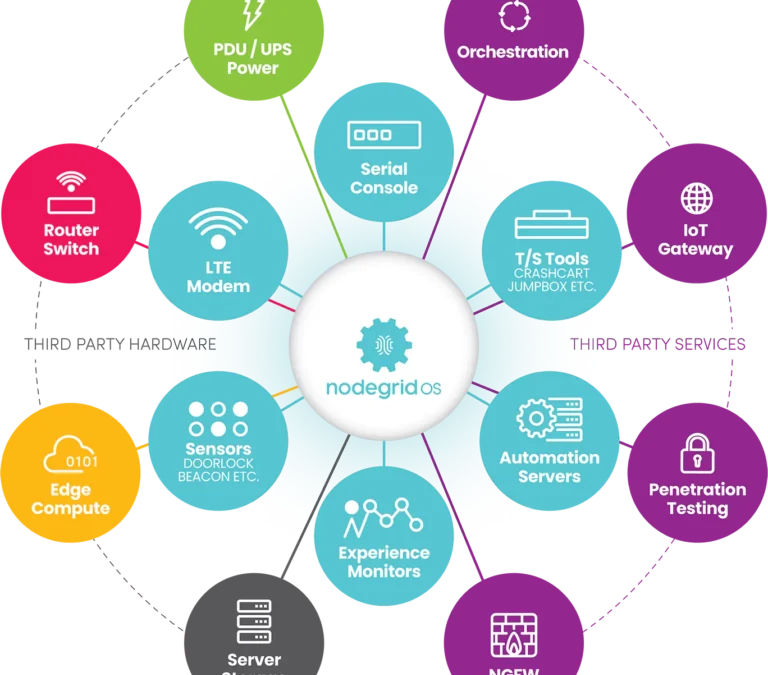
ZPE Systems’ Services Delivery Platform accelerates time-to-market
ZPE Systems’ Services Delivery Platform accelerates time-to-market with any app, anytime, anywhere IT teams can deliver instant business value with the on-demand services delivery architecture...

Zero Touch Deployment Cheat Sheet
This post provides a “cheat sheet” of solutions to the most common zero touch deployment challenges to help organizations streamline their automatic device provisioning.

ZPE Systems Partners with Atsign to Add Zero Attack Surface Technology
ZPE Systems has partnered with Atsign. Read the press release to learn more about zero attack surface technology.
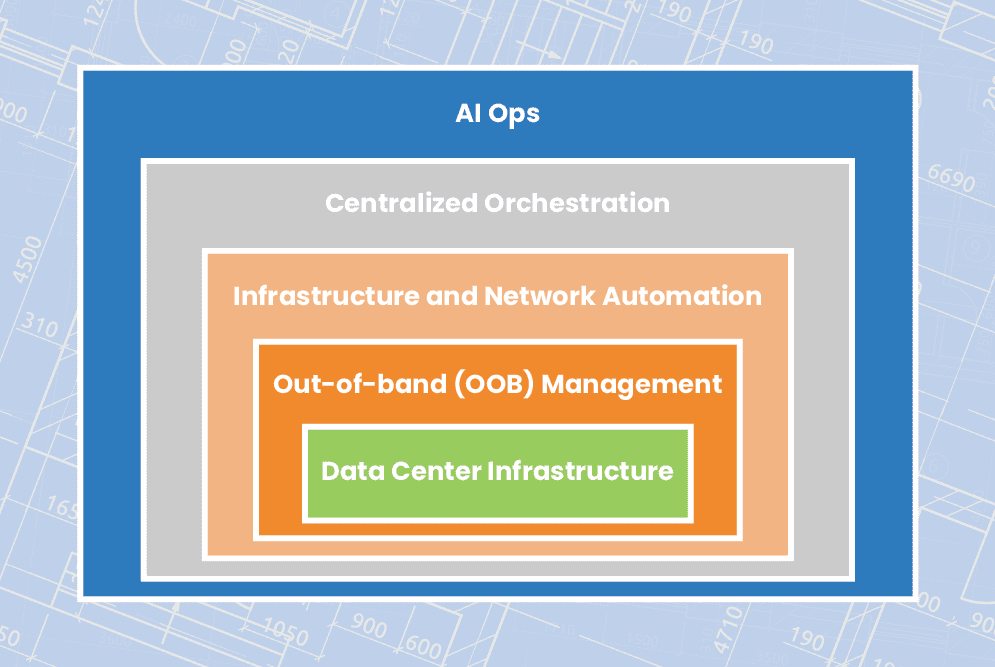
Streamlining Remote Data Center Management
Learn how to streamline remote data center management using technologies like OOB management, automation, orchestration, and AIOps to ensure network resiliency.

ZPE Systems keeps first responders mission-ready with FirstNet certification
ZPE Systems is now FirstNet certified. Read the press release here to see how we’re keeping first responders mission-ready.
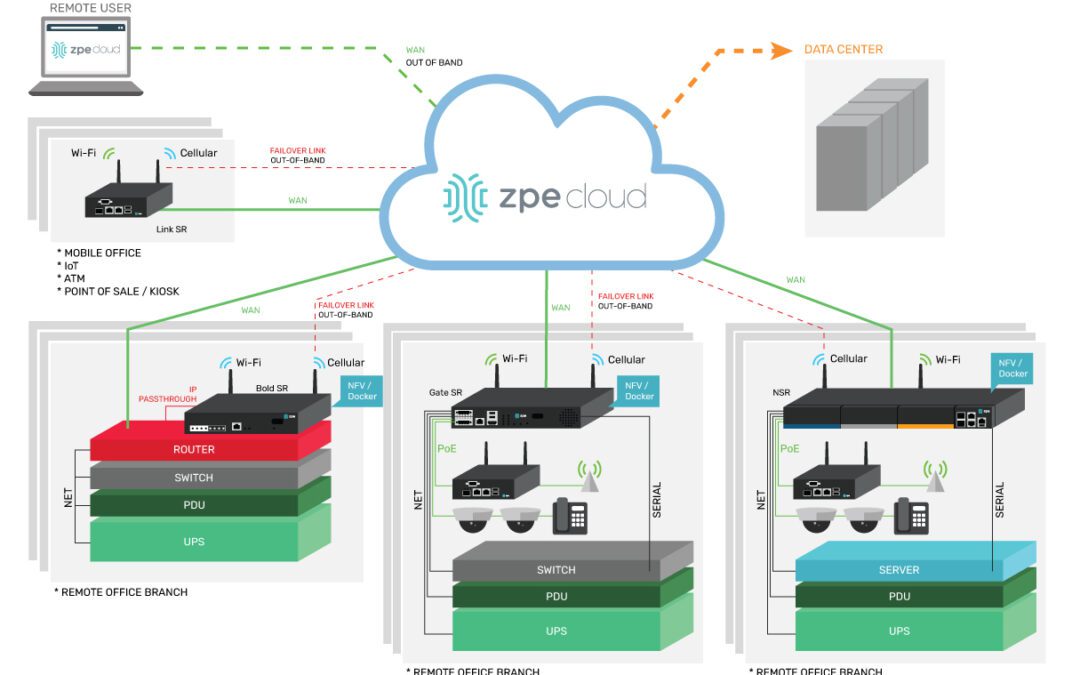
Cloud-Delivered Branch: Simplifying Remote Management
Describing the three cloud-based services involved in a cloud-delivered branch and illustrating how to implement a cloud-delivered branch with Nodegrid.
3 Gaps That Will Leave IT Teams Scrambling
Today’s IT teams must maintain a growing infrastructure of on-prem and cloud solutions. These range from physical routers, out-of-band devices, and firewalls, to Zero Trust Security solutions,...
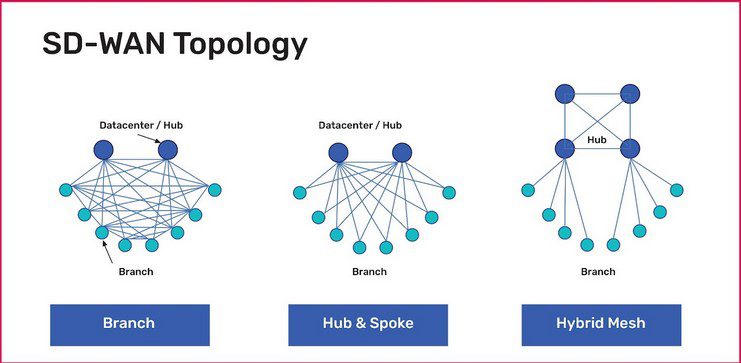
A Guide to SD-WAN Deployment Models
Learn about the most common SD-WAN deployment models with diagrams, pros and cons, and best practices to help organizations choose the right topology.

How to build an isolated recovery environment (IRE)
An isolated recovery environment (IRE) uses designated network infrastructure and survivable data to help teams recover from ransomware faster and with less impact to the business.

SD-WAN Benefits: Your Definitive Guide
SD-WAN benefits organizations through MPLS cost reduction, improved WAN performance, greater automation & orchestration, and enhanced security capabilities.
Simplifying Retail Network Management
Compact, all-in-one branch gateways use environmental monitoring, OOB management, and vendor-neutral platforms to simplify retail network management.
Network Automation Tools To Offset the Tech Talent Shortage
Network automation tools help organizations ensure the continued availability and performance of enterprise networks by streamlining workflows and reducing manual intervention.

The Importance of Remote Site Monitoring for Network Resilience
A centralized, automated OOB remote site monitoring solution helps to ensure network resilience even when recessions, pandemics, and other unforeseen events affect staffing on network teams.

Vapor IO: Re-architecting the Internet
Vapor IO is re-architecting the Internet with micro edge data centers. See how Nodegrid trims costs with automation & lights-out management.

What To Look For in an Environment Monitoring System
An environment monitoring system should include features like cloud management, vendor freedom, advanced security, and out-of-band management.

LTE Failover vs. LTE Out-of-Band
Cellular data networks can be used for LTE failover as well as remote out-of-band management, but these two technologies provide different capabilities.

White Box Networking: Making the Switch
Though white box networking has many advantages in theory, a lot of companies find it hard to achieve these benefits in practice. Here’s how to build a solution that avoids common pitfalls.

Why You Need an Out-of-Band Cybersecurity Platform
An out-of-band cybersecurity platform uses OOB infrastructure, vendor-neutral management software, and end-to-end automation to provide holistic network security.
Building an IoT Device Management System
An IoT device management system is meant to simplify and streamline the management of remote, hard-to-reach, and complex IoT devices and infrastructure.

Nodegrid OS Version 5.8 – Product Updates
Watch as Director of Solution Engineering Rene Neumann walks you through Nodegrid OS v5.8 and how it supports the Network Automation Blueprint. Rene shows you how v5.8 enables essential building blocks of the blueprint, including out-of-band management, visibility, out-of-band automation, and security.

Nodegrid OS version 5.6 – Product Update
Director of Solution Engineering Rene Neumann walks you through the updates of Nodegrid OS v5.6, including how they help you with site deployment and edge computing.

Nodegrid OS Version 5.4 New Features
Watch this video to see the new features in the latest release of Nodegrid OS, version 5.4. Sales Engineering Manager Rene Neumann shows you how to use the newest features.

What To Look for In a Cloud Edge Gateway Solution
The best cloud edge gateway solution is vendor-neutral, uses cellular for failover and OOB management, follows Zero Trust best practices, and supports major automation tools and scripting languages.

Uplogix 5000 Local Manager EOL Best Replacement Options
The LM83X is a direct replacement for the Uplogix 5000 Local Manager EOL model, which means it comes with the same base capabilities and suffers from the same limitations.

Implementing a Network Modernization Strategy for Large-Scale Organizations
The infrastructure orchestration and automation layer contains the tools and paradigms used to efficiently manage and control an automated network.

Using AIOps and Machine Learning To Manage Automated Network Infrastructure
Let’s discuss how AIOps and machine learning help teams manage their automation and orchestration—and the massive amounts of data produced by their automated systems—more efficiently.
A Guide to Infrastructure Orchestration and Automation
The infrastructure orchestration and automation layer contains the tools and paradigms used to efficiently manage and control an automated network.

Key Automation Infrastructure Components That Enable End-to-End Network Automation
As part of a resilient network automation framework, the most important automation infrastructure components include OOBM, SD-WAN, monitoring, IaC, and immutable infrastructure.

How an IT/OT Convergence Strategy Accelerates Network Automation
An IT/OT convergence strategy brings information technology and operational technology together under one management umbrella to create a unified, efficient, and resilient network infrastructure.

Driving the Hyperautomation Narrative Through Collaboration: An ONUG C-Level Series
Arnaldo and Mark discuss the importance of creating an observability strategy when architecting Hyperautomation solutions in the future.

Customer Case Study: 100% Network Availability for DigiCert
How does DigiCert achieve near 100% network availability? DigiCert’s Aaron Lott explains how ZPE Systems’ Nodegrid improves network uptime and cuts man-hours 50%.
Nodegrid Serial Console Plus: Gen 3 Out-of-Band at Scale
Still adding point products and hoping for better edge computing? It’s time to get Nodegrid with SASE (Secure Access Service Edge), so you can offer secure network access to every edge connection.

Nodegrid Gate SR: Versatile Services Router for Critical IT
For critical IT, the Nodegrid Gate SR enables more than networking and connectivity. This powerful services router features a variety of interfaces to enable remote out-of-band management of your sites. Connect to servers, routers, switches, USB devices, sensors, PoE appliances, and IoT with a single box.

What Is Edge Computing for Machine Learning?
Edge computing for machine learning places ML applications closer to remote sources of data, such as IoT devices, “smart” industrial systems, and remote healthcare systems.

Comparing Cellular Failover Router, Gateway & Bridge for Business Continuity
Cellular failover routers, bridges, and gateways offer similar capabilities, so here’s what you need to know about all three to find the best option for your business continuity.

The Growing Role of Hybrid Cloud in Digital Transformation
Vendor-agnostic platforms, SD-WAN, and automation are key tools that help organizations more effectively utilize the hybrid cloud in their digital transformation journey.

The Importance of Out-of-Band Data Center Connectivity
Here we dig into the causes and effects of data center outages according to the Uptime Institute report and discuss how OOB data center connectivity can help

What Is uCPE, and How Does It Benefit Enterprise Customers?
A renewed enthusiasm for uCPE has been led by a greater interest in software-based networking and a need for hardware capable of running that software.

Network Engineers: 5 Must-Have Tools During a Slow Economy
Network engineers need to make the most of their tools during a slow economy. Read on for five must-have tools for keeping services online.

ZPE Systems launches smartphone-size cloud gateway for IoT, OT, & IoMD applications
ZPE Systems released the Mini SR, a smartphone-size cloud gateway for IoT, OT, & IoMD. Read the press release for details & use cases.

Upgrade Network Infrastructure With Minimal Business Interruption
Vendor-neutral management devices, platforms, and ZTP allow you to upgrade network infrastructure with minimal business interruption.

The Definitive SD-WAN Security Checklist for Enterprise Networks
Software-defined wide area networking, or SD-WAN, has made it possible to efficiently control highly distributed WAN architectures using software abstraction and automation. SD-WAN adoption is...

How To Keep Colocation Data Center Pricing in Check
How to keep colocation data center pricing in check through consolidated devices, DCIM power management, SDN, and out-of-band management.

3 Gaps That Will Leave IT Teams Scrambling This Winter
IT teams will face three big gaps this winter. Read on to see what they are & how to close them for good with a proven network blueprint.

Why Cybersecurity-as-a-Platform (CaaP) is the Future of Holistic Security | ZPE Systems
There are challenges with managing a complex cybersecurity environment. Here is how Cybersecurity-as-a-Platform (CaaP) can help.

How SASE Technology Defends Your Network Edge
SASE technology connects network edge resources directly to cloud services, reducing the load on the main firewall without sacrificing security.

Creating the Future of Network Automation
Data center management best practices like IaC, automation, orchestration, and environmental monitoring contribute to NetDevOps. success.

Data Center Management Best Practices for NetDevOps Transformation
Data center management best practices like IaC, automation, orchestration, and environmental monitoring contribute to NetDevOps. success.

Data Center Colocation Services: Best Practices for Managing Remote Infrastructure
Manage data center colocation services more efficiently through solutions like environmental monitoring and OOB serial consoles.

Zero Trust Network Access vs. VPN for Branch and Edge Networking
ZTNA is the superior choice for branch and edge networking because of its security, speed, and scalability.

Solving Remote IT Infrastructure Management Challenges With Gen 3 Out-of-Band
Here’s how to solve remote IT infrastructure management challenges using Gen 3 OOB for high-speed remote access, environmental monitoring, and orchestration.

ZPE Systems Featured in L’Informaticien Magazine
ZPE Systems is featured in L’Informaticien Magazine. Read the translation here and check out the original source content.

CIOs: Tempos difíceis estão chegando. 3 Resoluções diretivas para sobreviver ao inverno da Recessão e Lockdowns
O índice da bolsa de valores Dow caiu mais de 1000 pontos nesta última sexta-feira de agosto. O mesmo efeito ocorreu em todas as bolsas de valores do mundo. Companhias como Apple, Vale, Google e...

Data Center Orchestration with Gen 3 OOB for Digital Services Providers
Here’s how data center orchestration with Gen 3 OOB management helps digital service providers achieve the reliability their customers demand.

CIOs: 3 Boardroom Questions to Survive Winter Recession & Lockdowns
CIOs: How will you make it through the winter recession? Read on for three key questions to answer & discover the blueprint for a proven resilience strategy.

Opengear CM7100 Alternative Options
Discussing Opengear CM7100 replacement options that deliver 24/7 availability, end-to-end automation, Zero Trust Security, and complete vendor freedom.
ZPE Cloud – Silver Peak and Palo Alto Networks Edge Deployment
Want to know how to set up a Silver Peak appliance and Palo Alto Networks firewall? In our latest video, Director of Solution Engineering Rene Neumann walks you through how to easily create an edge platform using the Nodegrid Gate SR and ZPE Cloud.
Reliable Infrastructure for the Internet Association of Australia
The Internet Association of Australia provides Internet exchange infrastructure across the country. Read the full case study to see how they offer reliable services.

Opengear Alternatives: Replacing the ACM7000 Resilience Gateway
Wondering about Opengear ACM7000 or Opengear alternatives on the market? Read this post to find out more.

How Enterprise Network Security Software has Evolved for the Edge
Protecting modern distributed edge networks have its challenges. Discover how the Noregrid SD-WAN solution can help you.

Actualizing Edge Computing Benefits in Your Enterprise
There’s no doubt that edge computing comes with benefits and challenges. Find out how Nodegrid helps you actualize edge computing for your enterprise.

Comparing In-Band Management VS OOB Management
We answer all your questions about In-band management vs Out-of-band management and more in our 2nd blog Reddit Response series.

What is a Serial Console’s Role in Modern Enterprise Networks?
What is a serial console’s role in modern enterprise networks? Gen 3 serial consoles provide greater control, security, and end-to-end automation.

What Is Hybrid Cloud Infrastructure: Expectations vs. Reality
What is hybrid cloud infrastructure, and how is it achieved? Comparing the expectations vs. reality of hybrid cloud with solutions to common problems.

Ingram Micro Signs Distribution Agreement with ZPE Systems
Ingram Micro Signs Distribution Agreement with ZPE Systems for Belgium, Netherlands, Luxembourg The Netherlands, July 18, 2022 -- Ingram Micro today announced a partnership with ZPE Systems Inc., a...

Nodegrid OS Version 5.6 – Product Updates
The goal of every release is to reduce complexity and improve security for our customers, and the new Nodegrid OS version 5.6 is no different. Some of the improvements which we implemented in...

Making Deployment and Management Easy for a Large Retailer
Simplified retail edge & critical remote access Making deployment and management easy for a large retailer A major retail company requires networking that can keep up with demand. However,...

Opengear Operations Manager Alternative Options
This blog reviews the Operations Manager platform before discussing Opengear alternatives that provide greater automation, security, and branch networking capabilities.

How to Use a Cloud Managed Gateway Router to Optimize OT Automation
Discover how Nodegrid’s cloud managed gateway routers deliver powerful edge network management for operational technology automation.

The Benefits of Vendor Agnostic Platforms in Network Management
There are two basic approaches to choosing a network management platform: you can stick with a single vendor’s ecosystem of supported products, or go with a vendor agnostic platform. In this post,...

Part 2: Immutable Infrastructure: Best Practices for Network Professionals
Immutable infrastructure involves servers, network appliances, and other devices which are never updated or changed. In part 1 of our blog series, we discussed the most inherent challenges with the...

Cisco Live tips to help you make the most of the show
Whether you’re a newbie or a veteran, these Cisco Live tips can help you get the most out of the show. It’s been a couple years since the last event, and our team wanted to give you some expert...

Cisco Live: ZPE Systems Unveils Automation Blueprint for ~100% Network Uptime
Las Vegas, NV Jun 14, 2022 -- ZPE Systems, the leading provider of out-of-band management to global tech giants and enterprise business, unveiled its platform for ~100% network uptime and...

Part 1: Immutable Infrastructure: Challenges Your Company Needs to Be Aware of
Immutable infrastructure refers to the critical network resources and systems that make up your infrastructure and that are never updated, changed, or fixed in any way—they stay exactly the same. If...

Why cybersecurity can make you feel lost in space
Cybersecurity has been a hot topic for years. With many high-profile breaches, malware attacks, and pricey payouts, it’s no wonder why companies continue to add more and more protection for their IT...
Supply Chain Security Risk Management Best Practices
A supply chain attack is when cybercriminals breach your network by compromising an outside vendor or partner. Often, these attacks exploit a weak link in your trusted ecosystem of third-party...

Why You Need a Next-Gen OOB Console Server
An OOB (out-of-band) console server is a fundamental data center tool that allows you to view, manage, and troubleshoot critical remote infrastructure on a dedicated network connection. While the...

Network Disaster Recovery Plan Checklist
Your organization may feel secure now, but a disaster could occur at any moment. For example, the war in Ukraine took the world by surprise and left many organizations scrambling to protect and...

What does 2001: A Space Odyssey have to do with network automation?
“I’m sorry, Dave, I’m afraid I can’t do that.”Those nine words couldn’t possibly be related to network automation. Or could they? Uttered famously by fictional supercomputer HAL 9000 in the 1968...
Orchestrating Hybrid Network Environments: Challenges, Solutions, and Best Practices
A hybrid network environment combines infrastructure from a public cloud with a private cloud and/or on-premises deployment. Your compute, storage, and service resources are distributed across...

Hyperautomation vs Automation: How Are They Different?
Automation can help you streamline network management in your enterprise by reducing human error, speeding up processes, and facilitating NetDevOps. Hyperautomation takes things a step further by...

How to Choose Secure Out-of-Band Management
Out-of-band access gives you an alternative path to manage your critical remote infrastructure at data centers, branch offices, and other distributed locations. However, that management link creates...

Network Automation Best Practices to Implement in 2022
As enterprise networks grow more complex and distributed, the need for network automation is rising. Automation can help you manage your network more efficiently, but only if you use it correctly....
O que é EDGE COMPUTING e como ele pode reduzir seus custos de TI?
Edge Computing ou Computação de Borda trata-se do processamento de dados mais próximo ao usuário local, criando maior fluidez e rapidez. É uma arquitetura de TI distribuída, onde os dados dos...
Por que usar a solução de SD-WAN?
As soluções de SD-Wan chegaram para mudar o paradigma advindo do risco de uso de links de internet para conectividade entre empresas e filiais. Ela é uma solução que integra muitas características e...
Você sabe quanto custa para a sua empresa um servidor fora do ar?
Quando o seu servidor para de responder, está “fora do ar”, toda sua empresa sofre as consequências e fica “fora do ar” Não é a apenas a área de TI que está com problemas, mas sim a empresa inteira...
Branch-in-a-Box: Why All-in-One Devices Are the Future of Networking
A branch network consists of many moving pieces that need to be remotely deployed, managed, and supported. That typically means separate devices for all the key functions like routing, switching,...

Top Data Center Infrastructure Management (DCIM) Trends of 2022
Data center infrastructure management (DCIM) keeps evolving to address enterprises' changing goals, requirements, and concerns. We spoke with DCIM sales engineers to find out which pain points are...

Automating Your Network Operations Does Not Have to Be Difficult
The importance of network automation is clear—you can reduce human error, create more efficient workflows, and streamline operations. However, many enterprises delay their automation efforts because...

How to Choose the Best Branch Office Connectivity Solution for Your Network
Branch network management involves many moving parts. For example, you may need to remotely deploy, orchestrate, and troubleshoot the branch network without on-site IT staff. In addition, you need a...

Vertiv Avocent ACS EOL: Choose Your Replacement Option
Vertiv discontinued their Avocent ACS6000 line of serial console servers at the end of 2018 and will stop supporting them on July 31, 2023 (or whenever your warranty expires). The Vertiv Avocent ACS...

How to Achieve Network Security: 4 Essential Steps for IT Professionals
How critical is network security today?. According to IBM, the cost of a data breach rose to $4.24 million in 2021, and that figure continues to rise. In this blog, we’ll describe how to achieve...

ZPE Systems Announces TD SYNNEX Partnership to Bolster Growth Strategy
Fremont, CA March 17, 2022 -- ZPE Systems Inc., a leader in network infrastructure management and orchestration solutions, today announced a partnership with TD SYNNEX (NYSE: SNX), a leading global...

Data Lake Use Cases for Edge Networking
Data lakes are a powerful tool for capturing, storing and analyzing data from many different sources. A data lake provides an inexpensive, flat storage architecture in which to house massive amounts...

Data Center Temperature & Humidity Best Practices: A Complete Checklist
Temperature and humidity have a significant impact on your data center infrastructure. High temperatures can cause devices to overheat, whereas extreme low temperatures can cause mechanical and...

Customer strategies in Ukraine to protect privacy and IP
How autonomous decommissioning via out-of-band has become essential to disaster recovery for edge deployments in uncertain geographies To say there’s instability in Eastern Europe would be a drastic...

ZPE Systems named Rahi Partner of the Year
ZPE Systems has been named Rahi’s 2021 Partner of the Year. The company outperformed more than 400 Rahi partners by excelling at revenue attainment, customer satisfaction, and support, among other...
Why Out-of-Band Remote Access is Critical for Branch Networking
Branch locations—retail stores, shipping warehouses, and satellite offices—present a big network management challenge to the engineers supporting them. Traditional remote network management requires...
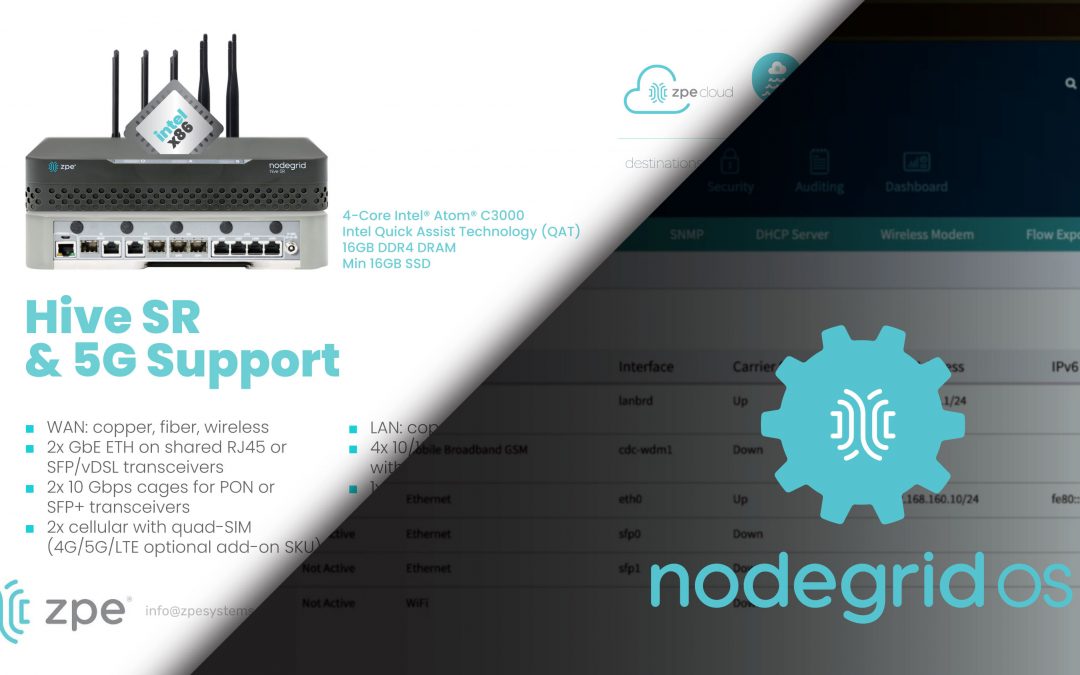
Nodegrid OS Version 5.4 New Features
Sales Engineering Manager Rene Neumann walks you through the new features in Nodegrid OS v5.4. Don’t miss these out-of-band and security updates.
Data Center Environmental Risks & Practical Solutions That Can Save You Millions
Today, many businesses are completely unable to operate without their data center infrastructure, so data center downtime is getting more and more expensive. According to Uptime Institute’s 2021...

What Makes a Gen 3 Serial Console?
The Gen 3 serial console is the latest innovation in out-of-band management.But what exactly is it, and where did it come from? In this post, we’ll briefly cover the basics of serial consoles and...
Benefits of SD-WAN for Hybrid Cloud Infrastructure
Hybrid cloud—using a combination of public and private clouds to host your data, applications, and services—is one of the most popular enterprise infrastructure models. According to Flexera’s 2021...

Data Center Environmental Monitoring: How to Stop Disaster Before It Strikes
Environmental threats—such as heat, moisture, power, smoke, and tampering—constitute a significant cause of data center downtime. According to a recent ITIC survey, a single hour of downtime could...

Q&A With a 20-Year DCIM Expert
Data center infrastructure management, or DCIM, involves monitoring and controlling the infrastructure within a data center. That means supporting the appliances and the underlying...

Data Center Environmental Monitoring: How to Stop Disaster Before It Strikes
Environmental threats—such as heat, moisture, power, smoke, and tampering—constitute a significant cause of data center downtime. According to a recent ITIC survey, a single hour of downtime could...

Network Field Day 27
Join us for Networking Field Day 27! Watch a live demo of Gen 3 Out-of-Band and our Zero Pain Ecosystem. Live stream at 8am Pacific, Jan 26, 2022. Don’t miss it!

NetOps vs. NetDevOps vs. SecOps vs. EdgeOps: Your Guide to Navigating the Networking Terms
NetDevOps, SecOps, and EdgeOps are crucial components of a holistic and integrated approach to network infrastructure. However, the way each practice works to achieve this objective is not...

Why Choose Nodegrid as Your Data Center Orchestration Tool
Managing and orchestrating remote data centers presents a number of challenges, which is why you need the right tools for the job. Nodegrid as a data center orchestration tool is a family of...

Edge Computing Trends to Expect in the Post-Covid World
Over the last years, IT professionals have placed a larger focus on edge computing for businesses as they have increasingly turned to remote work in response to Covid-19. Because of this shift,...

Simplifying Network Edge Orchestration With a Single Platform
One of the most prominent edge computing challenges any organization may face is deploying and managing their critical remote edge infrastructure. For instance, the lack of network edge...

How to Reduce Data Center Carbon Footprints
Data centers face a uniquely modern challenge when it comes to climate. Government estimates place data center energy consumption at 10 to 50 times the energy per floor space of a normal commercial...

Watch agile networking in action with these Nodegrid demos
Watch agile networking in action with these Nodegrid demos ZPE® Systems Network Solutions Architect Rene Neumann shows you how easy it is to enable agile networking. See Nodegrid and ZPE...

Colocation Data Center vs. Cloud: Main Differences & Similarities
Implementing reliable and effective IT solutions to your network infrastructure is crucial to keeping pace with competitors, especially in today's fast-moving digital world. Whether your business is...

ZPE Systems introduces fully-integrated, open SD-Branch platform
ZPE Systems introduces Next-Generation SD-Branch for distributed enterprises and managed service providersFremont, CA, December 8, 2021 – Despite using SD-Branch and next-gen firewalls for branch...

SecOps Best Practices for Enterprises
SecOps is the blending of security and IT operations into one combined set of workflows, tools, and methodologies. This increases the speed at which new infrastructure can be spun up without...

The Importance of NetDevOps Automation for Modern Networks
The NetDevOps methodology is all about removing barriers and encouraging open collaboration between network, development, and operations teams. NetDevOps automation is what enables this...

HEAnet: providing network uptime for education
If there’s one sector that relies on network uptime more than ever before, it’s the education sector. For both in-person and virtual learning, students and staff connect to crucial resources...

NetDevOps Transformation Process & Critical Steps for Network Professionals
The NetDevOps methodology helps organizations streamline their network, development, and IT operations through automation and cross-team collaboration. This blog will explain the NetDevOps...

Security Service Edge (SSE) Implementation Guide for Enterprises
Security Service Edge (SSE) is an emerging network security model that rolls up technologies like zero trust network access (ZTNA), cloud access security broker (CASB), secure web gateway (SWG), and...

Top Security Service Edge Use Cases & Benefits for Enterprises
Security service edge (SSE) is an emerging network security model, first announced by Gartner in their 2021 Hype Cycle, that stems from the need to retool the industry’s thinking about SASE (secure...

Understanding Key Components of SSE (Security Service Edge)
Modern network management involves a wide variety of distributed technologies. Because of this, enterprises have progressively moved towards the Security Access Service Edge (SASE) model to provide...

How to Implement Zero Trust: Technologies to Shield You From Million-Dollar Losses
How to implement zero trust security is a growing focus of organizations across the globe. With cyber attacks frequently hitting some of the largest companies and threatening entire economies, it’s...

How Automated Network Management Helps in the Remediation of Human Error
Large enterprises rely on the management and administration of their networks to continue their daily operations. In recent years, networking trends have pointed towards using automated processes to...

What Is Zero Trust Security? 5 Critical Things You Need to Know
Zero trust security is not a new concept, but it has gained popularity in recent years. As companies become increasingly distributed, they must offer flexible network access without putting...

3 Data Center Management Challenges—and How to Solve Them for Good
Data center infrastructure adds an extra layer of complexity to enterprise networks since you need to remotely manage hardware at scale. The network perimeter needs to extend across a geographical...

Data Center Modernization Strategy: How to Streamline Your Legacy Environment
The rapid development of data center infrastructure management (DCIM) tools leaves most software quickly becoming outdated. Consequently, it is replaced by the next trend on the market, after a...

ZPE Systems hosts Palo Alto Networks’ Prisma SD-WAN for edge flexibility
Fremont, CA, September 21, 2021 – ZPE Systems, an innovator of network and critical IT infrastructure management at the data center and edge, today announced its ability to host Palo Alto Networks’...

SASE & Zero Trust: How They Come Together to Improve Network Security
How do secure access service edge (SASE) and zero trust work together to improve network security? Simply put, SASE works by deploying security via the cloud, and zero trust deploys security in the...

DigiCert: improving critical network infrastructure for 50% less work
Critical network infrastructure drives business. Like a system of roadways, it determines how efficiently communications move to and from your organization. This affects everything such as the speed...

SASE vs Security Service Edge: What’s the difference?
Security Service Edge. Is it just another fancy networking term? After all, we’ve already got SASE (Secure Access Service Edge), so why throw another buzzword into the mix? The truth is, there’s a...

3 Tips to Improve Edge Network Resilience
When it comes to improving edge network resilience, traditional WAN architectures can easily get in your way. Suppose you’re setting up an electrical substation, cellular base station, or other...

SASE Implementation: A Step-by-Step Guide for Businesses
SASE—which stands for secure access service edge—is a relatively new framework that converges wide-area networking with security into one cloud-based service stack. SASE uses software-defined wide...

The Importance of Micro-Segmentation for Zero Trust Networks
As workloads, applications, and data move to the cloud and business operations expand to include branch offices, remote data centers, and work-from-home staff, how do you define your network...

Detecting Ransomware on a Network: 3 Critical Steps to Ensure Network Security
Ransomware is one of the biggest threats to enterprise network security. Recent findings show that 37% of organizations were affected by ransomware attacks in 2020 alone. These attacks can be...

What Are the Key Zero Trust Security Principles?
Perimeter-based security is no longer sufficient for today’s enterprise network. You may even struggle to define your network perimeter anymore, mainly if you use cloud infrastructure, have remote...

Centralized vs. Distributed Network Management: Which One to Choose?
Though every business network is unique, they all broadly fall under one of the following architecture categories: centralized (or decentralized using server clusters) and distributed. Let's discuss...

Zero touch provisioning: 3 drawbacks you need to know
It’s Friday morning, and you’re bringing a new site online with zero touch provisioning. Your remote branch devices arrived the night before, and all you want the store manager to do is plug them...

Understanding Key SASE Components & Benefits
SASE—secure access service edge—combines SD-WAN technology with network security functionality into a single cloud-native solution. SASE uses SD-WAN’s intelligent routing to connect remote and...

ZPE Systems strengthens growth strategy with strategic hire
Fremont, CA, August 24, 2021 – ZPE Systems, an innovator of network and critical IT infrastructure management solutions, welcomes Steve Jehring as Vice President of Sales and Business Development....

Out-of-Band Network Management: Fundamental Principles & Use Cases
Out-of-band network management gives enterprises secure and remote access to critical network infrastructure, even during outages and service interruptions. It separates your production network from...

ZPE Systems announces Nodegrid Data Lake, app marketplace, and sensors to help organizations uncover valuable data for edge operations
Fremont, CA, August 10, 2021 – ZPE Systems launches a new applications marketplace, along with a portfolio of USB-type environmental sensors, meant to help organizations leverage valuable data...

The SASE Model: Key Use Cases & Benefits
Secure access service edge (SASE) is the recommended architecture for security and connectivity. SASE combines wide area network (WAN) technology for robust onramp to cloud and network security...
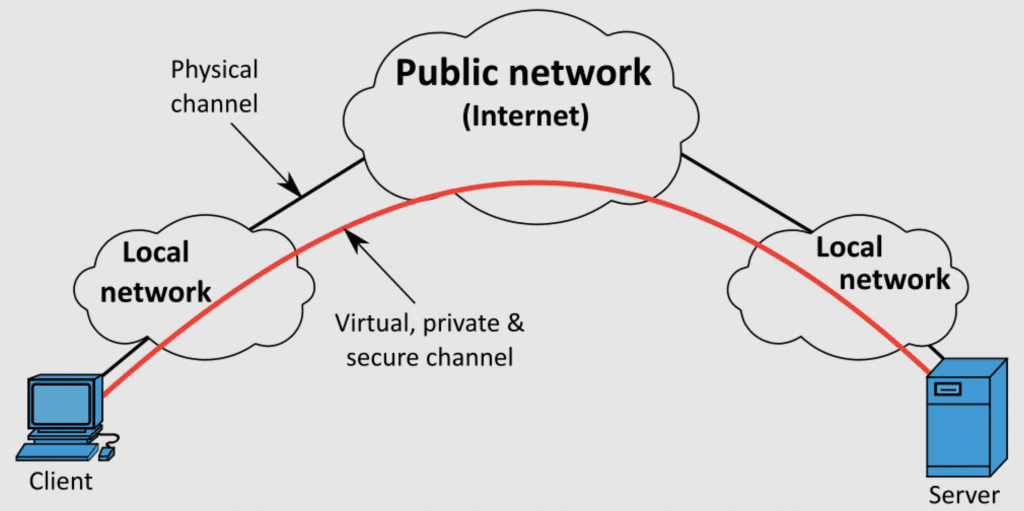
4 Things to Avoid When Choosing a VPN
Do you know what to avoid when choosing a VPN? These virtual private networks are commonly promoted as the key to online privacy and security, as they employ dedicated point-to-point connections,...

How to Implement a Zero Trust Security Strategy in an Enterprise Environment
Large enterprises may be hesitant to adopt zero trust security because it may seem too disruptive to their business. However, cyberattacks on businesses continue to increase, costing affected...

The Top 4 Network Management Issues Your Company Needs to Be Aware Of
Managing today’s enterprise network is more challenging than ever before. Most network infrastructure is no longer centralized, and we frequently need to incorporate cloud, SaaS, and other...

Zero Trust Security for IoT: How to Secure Your Network
The internet of things (IoT) is driving companies to rethink how they secure their networks. When you introduce unmanaged, internet-connected smart devices to your network, you’re also introducing...
3 Ways Your Critical Remote Infrastructure Is Costing You
It’s easy to imagine all the ways that downtime can throw a wrench into your critical remote infrastructure operations. Things like scaling, service outages, and tedious management are just part of...

ZPE Systems Announces Nodegrid Serial Console Plus, a High-density, Cellular-enabled Serial Console for Datacenters and Critical Remote Locations
Fremont, CA, June 22, 2021 – ZPE Systems adds to their lineup of datacenter infrastructure management solutions with the Nodegrid Serial Console Plus (NSCP). Like previous generations of Nodegrid...
Zero Trust Architecture: What to Know About the Latest Cybersecurity Executive Order and How to Implement It
Without a zero trust architecture in place, your business might suffer a setback of $4 million or more due to cybercrime. That’s how much the Colonial Pipeline recently paid out after hackers shut...

Out-of-Band Is a Lifesaver for Critical Edge Networking. Here’s Why …
The edge of the network is where local area networks make their connections to the edge of the Internet and to wide-area networks. Thus, edge networking serves edge computing, which brings...
Critical Remote Infrastructure and Why It Matters
Companies are finding it challenging, and sometimes difficult, to adjust to remote work. But “work from anywhere” (WFA) isn’t just a passing fancy, nor is it likely to subside even when the world...
Advanced Out-of-Band Management for a Major Media Provider
Out-of-band management brings critical connectivity to your network infrastructure. As a secure way to access your systems, out-of-band (OOB) helps you troubleshoot issues, patch devices, and...

Shifting Gears: How Network Automation Drove an Auto Company to the Cloud
Network automation and zero touch provisioning are more than luxuries. They’re quickly becoming the powertrain of business, helping you meet growth demands and keep up with important opportunities....

Improving Network Design for a Major Online Retailer
Out-of-band management is a critical component of network design. Instead of using one of your main networks for administrative tasks, out-of-band (OOB) gives you admin access via a completely...
Your 5-Step Checklist to Network Automation
How can you overcome the challenges of network automation?Network automation is key to simplifying administration. As infrastructures become increasingly complex, IT teams everywhere struggle to...
ZPE Systems Announces the New Edge Transformation Partner Program
Fremont, CA, March 31, 2021 – ZPE Systems, Inc., a leading innovator of network devices and cloud-based infrastructure management solutions trusted by the world’s top companies, officially launched...
What Is the Network Edge, and How Do You Manage It? Watch Our Webinar
What is the network edge? The network edge consists of systems that are not part of the data center. Think of a typical enterprise network: the data center is at the core, and then there are...

Webinar: Managing the Network Edge: Why your best practices need out-of-band management
Not at Cisco Live? Join our free webinar Setting up POPs, colocations, and remote networks is a lot of work, and ongoing maintenance sinks your resources. But out-of-band management and converged...

What Is Edge Networking, and Is It the Future?
We’re entering the era of edge networking Edge networking is critical to the future. Organizations continue to expand, and analysts predict that the data center won’t be the only workhorse when it...

Retail Cost Savings Using Network Consolidation
When it comes to infrastructure, network consolidation is becoming a must-have. This is especially true in hyper converged architectures, where streamlining operations means the difference between...

Virtual Customer Premises Equipment with Palo Alto Networks and Nodegrid
Virtual Customer Premises Equipment Virtual Customer Premises Equipment, or vCPE, is the epitome of network function virtualization. Enterprises are implementing this form of customer premises...

Investing in Out-of-Band Management to Reduce Risks
In the finance industry, network modernization protects the most confidential customer data. Whether for processing minor withdrawals & deposits, or recording asset transactions & real...
Edge Networking: Your 4-Step Checklist to Becoming Future-Proof
Why you need to focus on edge networking You may already be witnessing a shift toward more advanced edge networking. The industry is realizing the drawbacks of traditional core-to-edge...
How to Overcome 5 Challenges of Zero Trust Security
Zero Trust Security protects your enterprise inside and out. By safeguarding connections with approaches like traffic segmentation and multi-factor authentication, you can ensure total network...

Why You Need to Adopt Edge Networking
What does edge networking mean to your enterprise? Does it mean fast service delivery to hundreds of remote locations? Or smooth networking & security for your work-from-home staff? When your...

Optimize Edge Networking With This Free Guide to Out-of-Band, SD-Branch, & More
Edge networking continues to grow as a vital component to business. With more people working remotely, whether from home, in the field, or on the road, it’s now critical to have a network that goes...

ZPE Systems Recognized as 2020-2021 Intel Winners’ Circle Member
Fremont, CA, January 11, 2021 – ZPE Systems, Inc., a leading provider of network infrastructure management solutions, has been recognized by Intel Corporation as a 2020-2021 Winners’ Circle Member...

7 Reasons Why We Put Intel CPUs in the Nodegrid Serial Console
Intel® CPUs power many of the computers we use today. These include everything from personal desktops and laptops, to high performance computing clusters that aggregate power to solve major global...

See How Nodegrid’s Out-of-Band Eliminated EBRC’s Single Points of Failure
European Business Reliance Centre, or EBRC, requires out-of-band management capabilities to keep business running. As a managed services provider, EBRC helps companies outsource their IT efforts and...

4 Critical Things to Know About Zero Trust Security
Zero trust security is not a new concept, however it has gained popularity in recent years. As companies become increasingly distributed, they must offer network access that’s flexible, without...
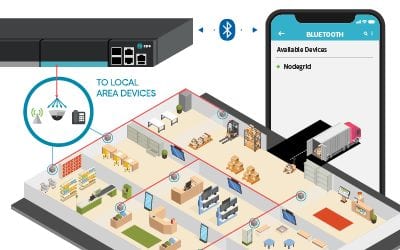
Provision Offline with Bluetooth Pairing for Nodegrid
Deployment day is here and it’s time to get your new remote branch up and running. Months of planning and preparation have gone into this project to ensure that everything goes smoothly. All of the...

Get Your Guide to Business Continuity with Out-of-Band Management
When business continuity is on your mind, out-of-band management should be, too. That’s because your network serves as the backbone of your enterprise. Whether you’re in retail, manufacturing, oil...

6 IT Solutions to Implement Right Now for More Effective Remote Work
Many companies have found it difficult to adjust to remote work. In the face of drastic changes brought on by pandemics, natural disasters, and other challenges, untethering your workforce from the...
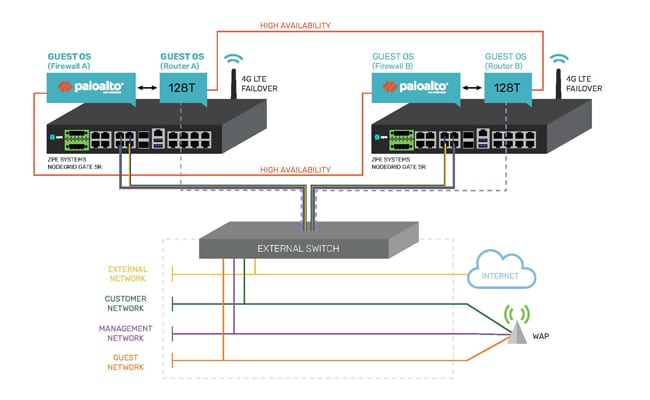
Secure Access Service Edge For an Oil & Gas Provider
Secure Access Service Edge is a new concept that’s transforming the edge network. SASE delivers more flexible and secure network access, so your business can adapt to drastic changes and accommodate...
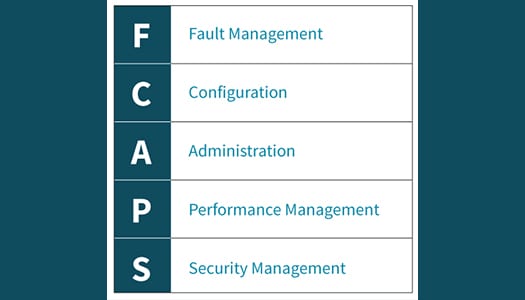
What is FCAPS?
What is FCAPS? Successful businesses rely heavily on their network infrastructure to keep up with demand and to allow work to flow smoothly. When outages occur, whole operations can come to a...
Help NetOps Teams Using Application Hosting & Guest OS
Application hosting helps your business become more flexible. This virtualization approach is a perfect solution if you’re looking to reduce your networking stack, make critical services more...

ZPE Systems and 128 Technology Announce Strategic Partnership
Fremont, CA, September 17, 2020 – Today, ZPE Systems, Inc., a leading provider of network infrastructure management solutions, and 128 Technology, Inc. (128T), a leading provider of software-defined...

How Nodegrid Improves Network Automation in the Test Lab
Is Your Test Lab Lacking Network Automation? Is Manual Testing Still Taking Up Resources? Without network automation, you’re familiar with having to spend time and resources on manual testing. You...
Automation: Reducing Costs and Improving Efficiency
As networks and data centers grow and become more advanced, the time and maintenance required to keep them operating at peak efficiency also increases. This leads to more engineers working more...
SD-Branch for a Digital Security Leader
SD-Branch delivers some major advantages over traditional SD-WAN capabilities. Where typical software-defined approaches fall short at the branch level, SD-Branch picks up the slack to help you see...
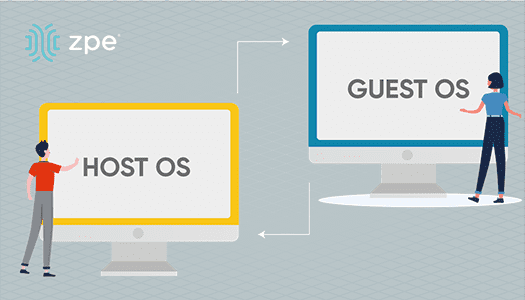
Your Application Hosting & Guest OS Checklist
Follow these simple steps to get started setting up your virtual network environmentApplication Hosting and Guest OS Alleviate Many Problems for NetOps Teams. You typically need to install and...

Case Study: SD-Branch for a Digital Security Leader
SD-Branch delivers some major advantages over traditional SD-WAN capabilities. Where typical software-defined approaches fall short at the branch level, SD-Branch picks up the slack to help you see...
Aging/Unsupported In-Band and Out-of-Band Infrastructure
Background/Problem A large distributed business enterprise with multiple data centers located around the globe, housing thousands of physical and virtual devices, routinely requires sysadmins to...
Easily Migrate from One Console Server Maker and VM Vendor to Many Vendors
Easily Migrate from One Console Server Maker and VM Vendor to Many VendorsBackground/Problem A few years back, this company standardized on a particular vendor’s console servers. On top of this,...

Providing a Safe Development Environment to Protect IP and Prevent Accidents
Providing a Safe Development Environment to Protect IP and Prevent AccidentsBackground/Problem Virtual Machines (VMs) and physical servers are located on the Telco’s production network. Their 1,000+...

Nodegrid Manager® – Multi-Vendor Viewer
Background/Problem A Global customer had to deal with various vendor solutions implemented throughout their infrastructure – The customer wanted a single point of management to provide access and...

Saving Serial Ports with Device Cascading
Background/Problem A top global networking company asked ZPE Systems for a high-density device with a very specific feature set. The customer needed a 96 port console solution that could do bulk...
High Density NodeGrid Serial Console™ Saves Space and Reduces Costs
Background/Problem A top global networking company asked ZPE Systems for a high-density device with a very specific feature set. The customer needed a 96 port console solution that could do bulk...

Connecting to Networking, Servers, and Power Devices within the Data Center
Background/Problem A web scale company needed a solution for their environment that would securely access and control networking, servers, and power devices. They needed LLDP to detect network...
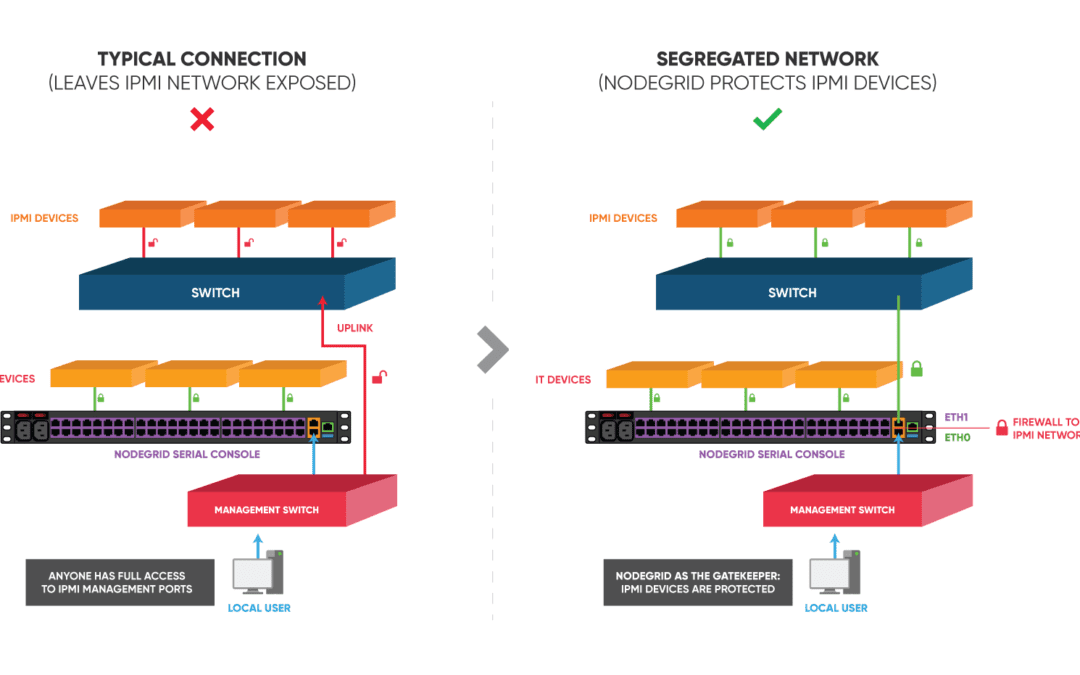
Protecting IPMI Networks with Nodegrid®
Protecting IPMI Networks with Nodegrid®Background/Problem A top financial organization was concerned about security problems with their IPMI management network. They were having to deal with...

Supporting the Financial Industry with Enhanced Out-of-Band Management
Background/Problem A Fortune 250 multinational financial services institution needed a replacement for their Cisco Integrated Service Routers that were reaching End of Life (EOL). The customer...

Enhanced Out-of-Band Management with Nodegrid
Background/Problem A Fortune 250 multinational financial services institution needed a replacement for their Cisco Integrated Service Routers that were reaching End of Life (EOL). The customer...
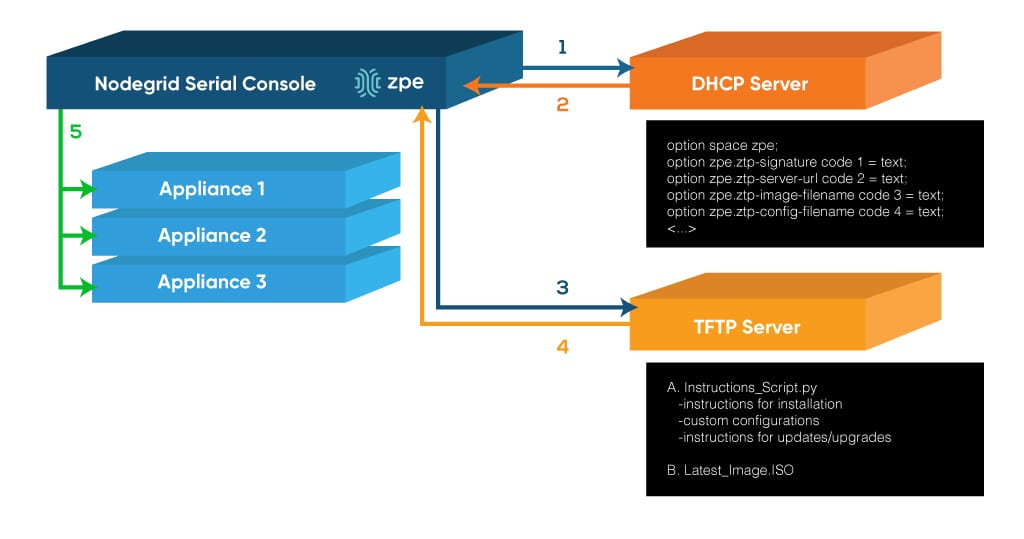
Zero Touch Provisioning (ZTP) for IPv4 and IPv6
Zero Touch Provisioning (ZTP) for IPv4 and IPv6Background/Problem Engineers are constantly looking for ways to improve their network infrastructures. These improvements can come in the form of...
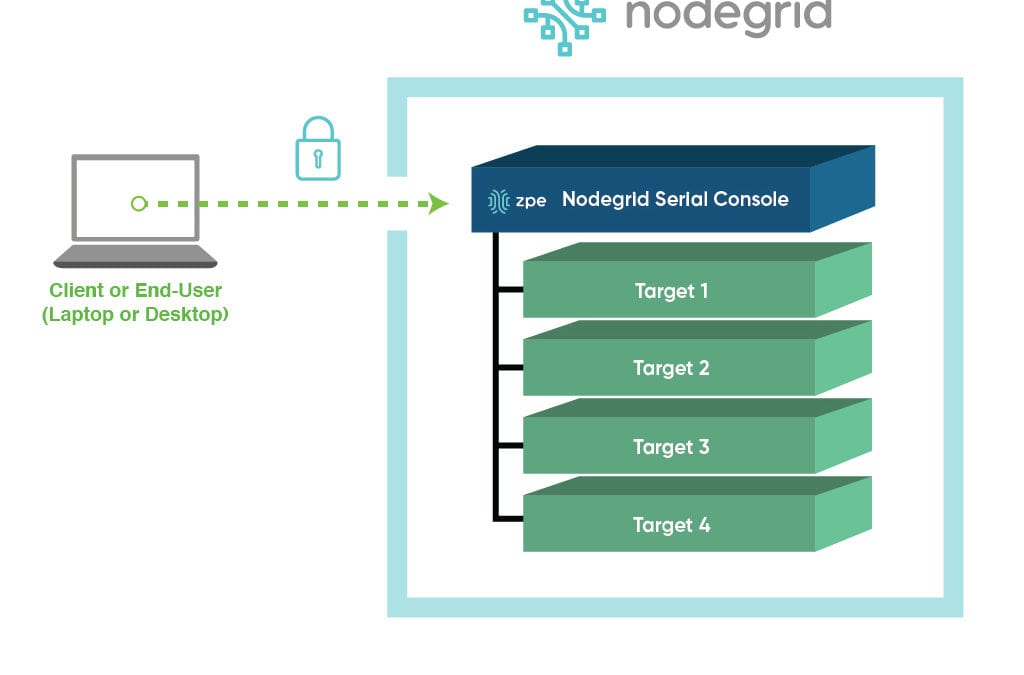
Securing your Network Infrastructure with Nodegrid
Securing your Network Infrastructure with NodegridBackground/Problem Network-based security attacks can jeopardize the integrity of your organization’s network infrastructure. As technology...

Better Application Hosting & Guest OS
Better Application Hosting & Guest OS As your business continues to expand, your infrastructure needs to adapt and grow to keep up with increases in demand. Rack space in your data centers comes...

ZPE Systems Announces Integration with Palo Alto Networks to Provide Enhanced Network Security
Fremont, CA, August 21, 2020 – Today, ZPE Systems, Inc., a leading solutions provider for network infrastructure management solutions, announced an integration with Palo Alto Networks to provide...

Secure Access Service Edge: What It Is, Why It Matters
Secure Access Service Edge (SASE): It’s one of those new-ish IT acronyms that many folks have heard about, but far fewer have actually used or really even understand it. But if you have remote and...
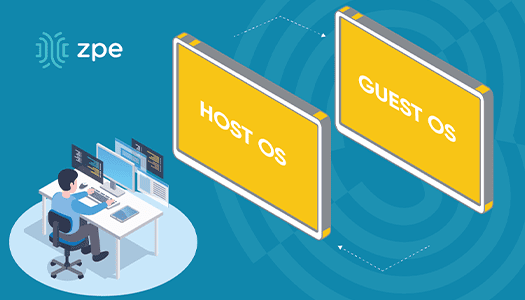
Transform Enterprise Network Operations With Application Hosting & Guest OS
Application hosting and guest OS are transforming enterprise network operations. With the ability to globally distribute software via the cloud and take advantage of applications regardless of...

Your 4-step Checklist to Reliable & Flexible Cellular Failover
Downtime can cost $300,000 per hour. But there’s a simple way to safeguard your business from expensive outages, and that’s by using cellular failover. When your T1, DSL, fiber, or cable connection...
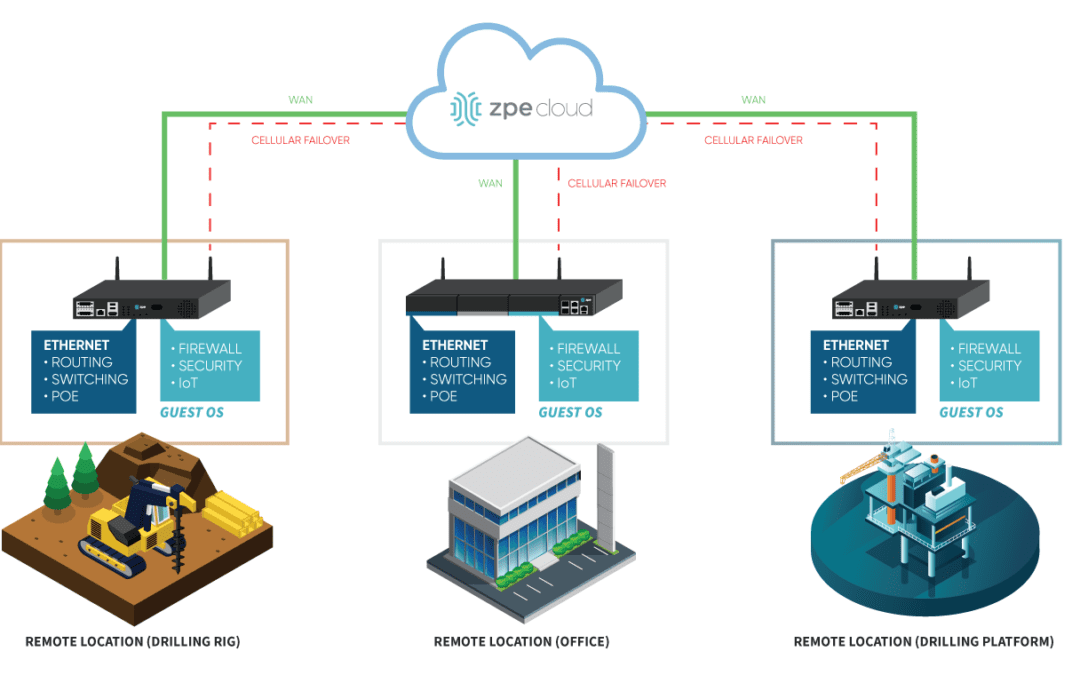
10 Things to Consider when Choosing a Branch Networking Solution
Branch networking is evolving. From the core to the edge, you need to consider so many factors, such as scalability, costs of deployment & maintenance, the speed of installation, and much more....

What is Cellular Failover?
Learn the basics of Cellular Failover in this 2 1/2 minute video. John Paul Kang, Solutions Engineer at ZPE Systems, shares his IT and data center expertise to provide a high-level overview of...
Best Practices for Deploying your Branch Network
Even if you’re familiar with these 10 things to consider when choosing a branch solution, you might not be sure about how to overcome the challenges of deploying branch networks. Here are some of...
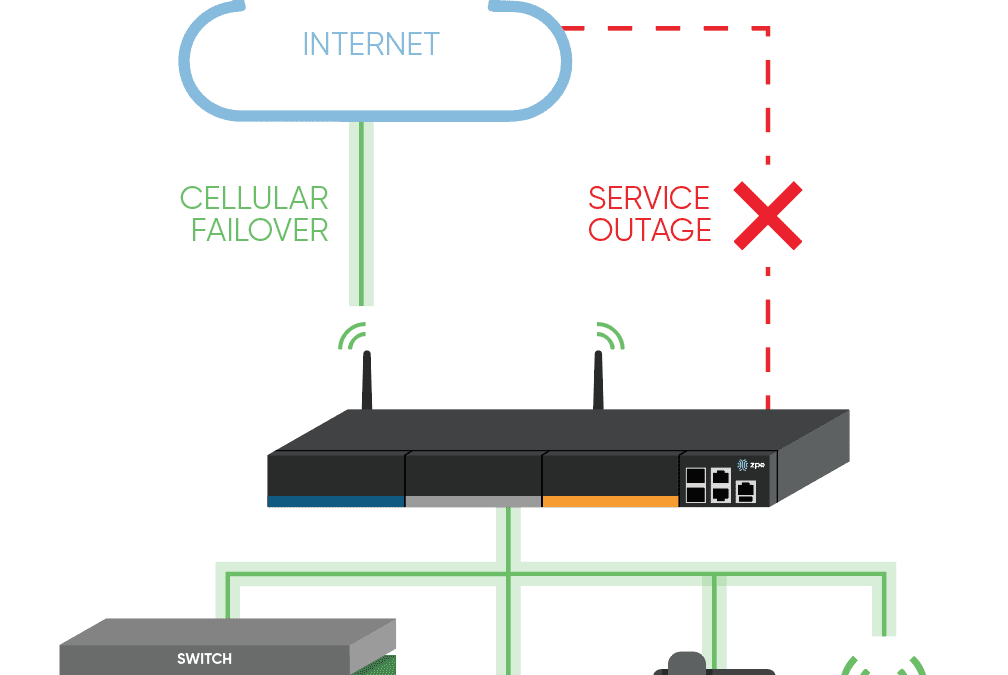
Why Your Business Continuity Plan Needs Cellular Failover
Cellular failover sets a new standard in high availability. When your primary WAN connection goes down, this wireless option keeps you safe from expensive outages. Compared to traditional redundancy...

Why Out-of-Band Management for the Branch is Better With Nodegrid
Out-of-band management (OOB) and business continuity go hand-in-hand. If set up properly, your OOB network should provide safe, reliable, always-ready access to your critical infrastructure...
How to Prepare for Cellular Failover
It’s 3AM and you’ve just been woken up by the sound of your phone ringing. As you struggle to shake off the drowsiness, you start to feel that all too familiar wave of stress wash over you. A...
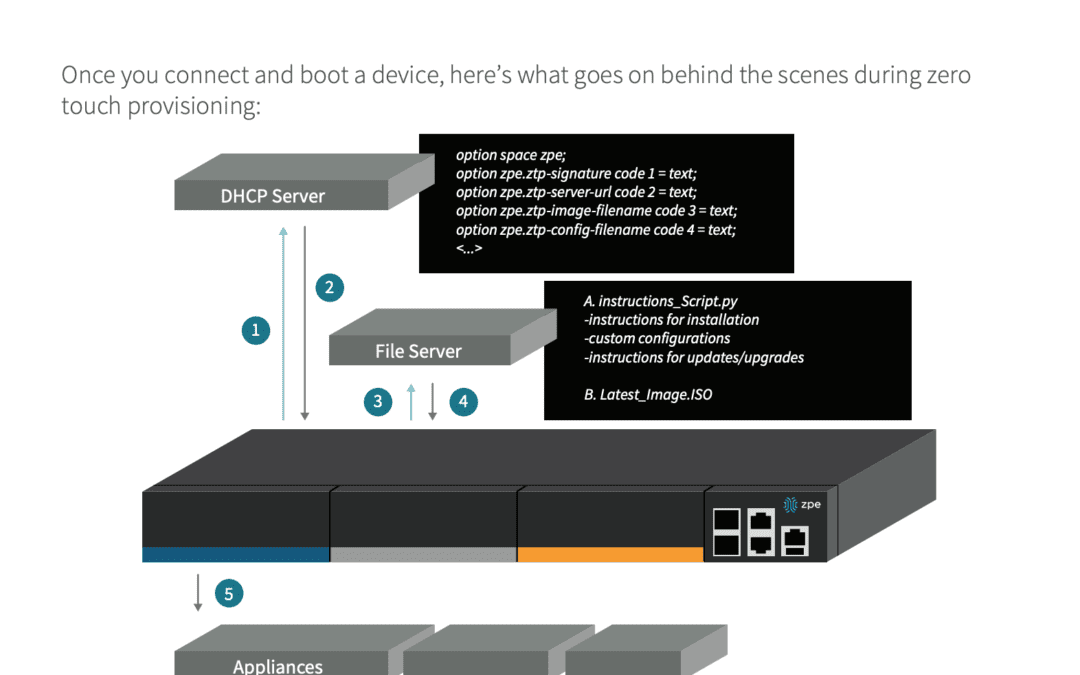
The Definitive Guide to Zero Touch Provisioning
It’s no wonder why zero touch provisioning (ZTP) is becoming more highly sought after. Whether business is expanding, going global, or simply in need of more nimble networking, ZTP sets the standard...
Benchmark Nodegrid Services Router
In these challenging times support staff demand secure remote access to critical infrastructure devices, as it accelerates troubleshooting and negates the need for on-site visits. There are plenty...

Keep Your Network Outage-Proof
You can’t control the weather, a pandemic, or natural disasters. But you can control network uptime with remote out-of-band management from ZPE Systems. Time and money hinge on your network. So what...
Webinar: Deploying Smart Edges to Support Modern Applications
About the Webinar: The advent of AR/VR, autonomous cars, smart everything, IoT, and other 5G applications requires processing of data at the edge of the network to shave off response times, manage...

How ZPE Systems Improves Secure Access Service Edge
Secure Access Service Edge transforms edge networking. See how ZPE Systems — a leading innovator in network infrastructure management — introduces even more capabilities to this...

4-Step Checklist for Setting Up Zero Touch Provisioning
Zero Touch Provisioning (ZTP) makes deployment fast, easy, and automatic. ZTP uses automation and scripting to eliminate expensive, time-consuming manual provisioning. Instead of spending days or...

What is Zero Touch Provisioning?
Learn the basics of Zero Touch Provisioning (ZTP) in this 2 1/2 minute video. Rene Neumann, EU Solutions Engineering Manager at ZPE Systems shares his IT and data center expertise to provide a...
A Closer Look: Zero Touch Provisioning Vs Manual Configurations
Our previous post about zero touch provisioning (ZTP) details the basics about what makes ZTP work. You need to have the proper scripting and automation tools, along with a well-designed workflow....
Maintain Branch Deployments Using the Cloud
The cloud — it’s great for delivering services and applications that are crucial to your business. It can help your continuity efforts by providing SASE solutions where you need most, and it can...

A Brief Introduction to Zero-Touch Provisioning
Another day, another deployment. Business is good and you’re scaling fast to keep up. This means opening more data centers, branch offices, and retail locations. Large or small, each deployment...
Understanding SD-Branch
This 90-second video explains how you can remotely take full control of your network with 360-degree visibility to all your devices. Learn how ZPE System’s Nodegrid appliances and vendor-neutral...
The Benefits of Cloud-based Deployment for Your Out-of-band Network
Your out-of-band (OOB) network can make scaling more bitter than sweet. Growing your business comes with exciting new opportunities, and you know how to set up your OOB connections for proper...

Serial Console Servers: 5 Reasons Why Your Business Needs Them
Today, businesses depend highly on IT, and they cannot afford to experience downtime. That’s why they need robust IT infrastructure. Robust IT infrastructure can ensure businesses do not experience...

OOBM: 4 Reasons Why You Need it for Your Business
The IT industry is rapidly growing. In 2020, spending on IT services reached almost $952 billion worldwide, with software accounting for the largest percentage of spending. However, while companies...
What Goes Into Zero Touch Provisioning?
Without zero touch provisioning (ZTP), setting up a new data center or branch location takes work. You know that along with all your new hardware comes plenty of manual input and configuration...

Managing a Remote Team
It Happened Overnight. One day it was business as usual. The next, we were scrambling to set up our home offices. COVID-19 meant even the largest companies had to figure out remote work. And they...
3 Ways the Cloud Improves Out-Of-Band Management at the Branch
3 Ways the Cloud Improves Out-Of-Band Management at the Branch For decades, out-of-band management (OOB) has been supporting business continuity needs for organizations of all sizes. It’s a...
3 Ways Docker Improves Network Management
Docker is the best way to deploy applications. There are several ways Docker improves network management. From being compatible with almost any programming language and machine, to its ability to...
Use These Best Practices to Set up Your Out-Of-Band Network
If you’ve read our previous post about out-of-band management 101, you know how important it is to have an out-of-band network. To recap, there are two methods you can use when managing your...
Maintain Uptime With a Reliable Data Center and Business Continuity
The data center and business continuity — these go hand-in-hand, as one relies so heavily on the other. Because your data centers are mission critical, an outage can bring down your network and your...

How One Unified Platform Gives You More Control Over Branch Networking,
Branch networking comes with its own set of challenges that can get in the way of normal operations. As a network engineer, you’re tasked with preventing business disruptions while simultaneously...

3 Reasons Why Your Business Needs Out-of-Band Management
Out-of-band management is an essential tool that should be part of your business continuity strategy. But What Exactly is Out-of-Band, or OOB? Your network is comprised of many devices and...
How Network Automation Improves Out-of-Band Management
Business Continuity: Why Better Networking Helps you Weather the Storm Even with an adequate out-of-band (OOB) management path established, managing your network infrastructure can still leave you...

The Role of OOB Management – Today and into the Future
In this 5 1/2 minute video Scott D. Lowe, CEO of ActualTech Media, talks about the importance of Out-of-Band Management to keep organizations’ IT up and running from anywhere even when your IT team...

ZPE Systems, Chatsworth Products Collaborate to Provide Network Managers with Out-of-Band Outlet Control and Monitoring Capabilities
ZPE Systems, Chatsworth Products Collaborate to Provide Network Managers with Out-of-Band Outlet Control and Monitoring Capabilities ZPE Systems’ Solution Now Fully Integrates with eConnect® Power...

Shield Your Business with Secure Access Service Edge (SASE)
Secure Access Service Edge (SASE) is quickly evolving how enterprises offer secure connectivity. As the modern workforce becomes increasingly distributed, you need to accommodate more branch...

Make Management More Secure and Easy with Single Sign-On
Managing many network devices and applications can be a chore, and a lot of this stems from having to manually authenticate with each. You typically need to keep a spreadsheet containing your...

10 Things to Consider when Choosing a Branch Networking Solution
10 Things to Consider when Choosing a Branch Networking Solution Branch networking is evolving. From the core to the edge, you need to consider so many factors, such as scalability, costs of...
ZPE Systems – A Smarter Vantage Point
ZPE Systems - A Smarter Vantage Point Today, as broadband services have become more reliable and cost-effective, companies are shifting from expensive MPLS links to SD-WAN, which promises firms more...
Control More of Your Network with SD-Branch
In recent years, SD-WAN has addressed enterprise networking challenges by virtualizing the components of traditional WANs. This software-defined approach offers greater reliability by using...

ZPE Systems Welcomes Michael Zabolitzki – Director of Sales, ZPE Systems Europe
ZPE Systems Welcomes Michael Zabolitzki - Director of Sales, ZPE Systems Europe Fremont, CA, September 19, 2019 – ZPE Systems, Inc., a leading provider of software-defined, vendor-neutral open...

Data Center & Branch Solutions Introduction
ZPE Systems’ Data Center and Branch Network Solutions.

Branch Solutions Introduction
Introductory announcement of ZPE Systems’ new Branch Networking solutions ZPE Cloud.

ZPE Systems Announces ZPE Cloud, Cloud Based Configuration and Management Platform for Branch Networks
In Addition, Two New Hardware Networking Solutions, Nodegrid Link SR and Nodegrid Gate SR, to Bridge the Gap Between Data Center and Branch Networks. Fremont, CA, June 6, 2019 – ZPE...

ZPE Systems Names Rahi Systems, 2018 Partner of the Year
Fremont, CA, April 30, 2019 – ZPE Systems, Inc. (www.zpesystems.com), a leading provider of software-defined, vendor-neutral open infrastructure management solutions, today announced the winner of...

How One Unified Platform Gives You More Control Over Branch Networking
Branch networking comes with its own set of challenges that can get in the way of normal operations. As a network engineer, you’re tasked with preventing business disruptions while simultaneously...

ZPE Systems Announces Initial List of Virtualized Network Function (VNF) Applications for Nodegrid SR Solutions
ZPE Systems Announces Initial List of Virtualized Network Function (VNF) Applications for Nodegrid Services Router and Nodegrid Bold SR Solutions Fremont, CA, January 24, 2019 – ZPE Systems, Inc....

Enterprise Networking Magazine Names ZPE Systems “Top 10 Networking Startups of 2018”
Enterprise Networking Magazine Names ZPE Systems "Top 10 Networking Startups of 2018" Edge Computing Increasing the Scope for Business In today’s day and age of cloud computing that firmly lies at...
ZPE Systems, Inc. Announces Litigation Settlement
Fremont, CA, February 22, 2019 – ZPE Systems, Inc., a California-based company that provides hardware and software products to control IT infrastructures, recently settled litigation brought against...

Are Public Switched Telephone Network (PSTN) Lines still the best Failover option?
Most of us still remember the sounds of an analog modem connecting to the ISP or back to the corporate office. These nostalgic sounds are a thing of the past as broadband connections have pushed...

10 Things to Consider when Choosing an Edge Solution
The edge is changing; CAPEX & OPEX costs, scalability, the number of devices and tools that make up the environment, and the speed of deployment, all need to be taken into consideration for the...

How Nodegrid Serial Console / Nodegrid Services Router can improve the Test Lab with Automation
Are you in a test lab that needs automation? Are you in a test lab that has automation, but you need to get more out of it? We can help. This situation seems to be quite common from what we’ve seen....

Data Logging, Alert Notifications and Actionable Data
When you’re the one responsible for critical infrastructure assets within the data center, you’ve got to be quick to respond and readily available to take care of any issues that might surface. What...
ZPE Systems, Inc. Announces Significant Litigation Victories
Fremont, CA, August 23, 2018 - ZPE Systems, Inc., a California-based company that provides hardware and software products to control IT infrastructures, recently obtained two significant favorable...

ZPE Systems and DataFrameworks Announce Strategic Integration Partnership
DataFrameworks’ ClarityNow Software Qualified for use on ZPE Systems’ Nodegrid Services Router Fremont, CA, June 12, 2018 - ZPE Systems, Inc. and DataFrameworks announced today the qualification of...

Introducing: Nodegrid Bold SR
ZPE Systems Unveils Nodegrid Bold SR – A Compact Form Factor Infrastructure Management Solution with Software-Defined Networking and Network Function Virtualization Capabilities for Out-of-Band...

CAPEX and OPEX… Are you Making the Right Considerations on Your Out-of-Band Expenditure?
When considering your new infrastructure management solution, your organization’s primary focus may be on Capital Expenditure (CAPEX), which refers to the initial cost to deploy a solution. Rarely...

Introducing: Nodegrid Services Router – A Modular x86 Appliance with SDN, SD-WAN, Networking Functions, DevOps, Compute and OOB Capabilities
Fremont, CA, June 27, 2017 - ZPE Systems unveils Nodegrid Services Router ™(NSR) - A modular x86 open framework appliance designed for software-defined networking (SDN), SD-WAN, network function...

ZPE Newsletter – April 2017
ZPE Newsletter - April 2017 Team ZPE will be at Interop ITX on May 15-19, 2017 - Stop by booth #532 to meet the team, grab a some prizes, and sign up for your chance to win a Google Home! Get...

The Case For Nodegrid Clustering
Background / Problem: A fortune 500 organization reached out to ZPE with a problem many organizations face when growing. They had multiple data centers around the world and were looking to...

Supporting The Financial Industry With Enhanced Out-of-Band Management
Problem A Fortune 250 multinational financial services institution needed a replacement for their Cisco Integrated Service Routers that were reaching End of Life (EOL). The customer wanted an...

ZPE Newsletter – March 2017
ZPE Newsletter - March 2017 Hello, We've been hard at work, improving upon everything you know and love about ZPE. In case you missed the press releases or the latest...

Take OOBI and OOBM to New Heights
Take Your Legacy OOBI and OOBM Solutions to New Heights - Simply, Quickly, and Cost Effectively Are you ready to bridge the management gap between legacy, current, and future IT infrastructures? If...

Announcement: Cisco ISR2900 Series – End of Life
Cisco Announces End of Production for ISR2900 Series Integrated Services Routers Cisco's ever popular ISR2900 Series of integrated service routers has reached end of life. Cisco suggests the ISR4000...

ZPE Systems Announces New Corporate Headquarters, Continued Global Expansion and Brand Redesign
Fremont, CA, February 7, 2017 - ZPE Systems announced today the opening of its new larger corporate headquarters in Fremont, California, and continued global expansion with the opening of ZPE Europe...

NodeGrid Serial Console T48S Announced
An Auto-switching Serial Console Server with USB Connectivity for Next-gen IT Solutions Fremont, CA, August 18, 2016 - ZPE Systems unveils NodeGrid Serial Console T48S, a next generation serial...

ZPE Systems Unveils NodeGrid Service Processor
A BMC management platform inspired by the Open Compute Project Las Vegas, NV, July 11th, 2016 — ZPE Systems unveiled NodeGrid Service Processor TM at Cisco Live! 2016 – An IPMI, BMC...

ZPE Systems Announces NodeGrid USB™
Fremont, CA, July 6th, 2016 — ZPE Systems unveiled (IP patented) NodeGrid USBTM - A truly unified solution designed for mobility development and testing environments. NodeGrid USB improves...

ZPE Systems Announces Two New Products for IT Infrastructure Management of IoT and Edge Devices
LAS VEGAS, NV, May 3rd, 2016 — ZPE Systems unveiled two new products for resilient IT infrastructure management of IoT and Edge devices at Interop 2016: NodeGrid Bold™ - a compact form factor...

Reducing Downtime and Saving Money with a Well-orchestrated Out-of-Band Infrastructure
A well-orchestrated Out-of-Band infrastructure (OOBI), or Remote Access and Control solution (as it’s sometimes called) is a vital component in the fight against downtime and lost revenue. Every...

ZPE Systems Announces 100,000th Port Shipment of NodeGrid Serial Console
FREMONT, CA, February 25, 2016 — ZPE Systems today announced the shipment of its 100,000th port of NodeGrid Serial Console since launching in April 2015. Its open modular design, fast x86 CPU and...
Smart Serial Console Servers Conserve Network Ports
NodeGrid Serial Console (NSC) is able to share network ports with fellow devices, sharply reducing network switch port usage for OOB device management. This new port saving feature is already...

Maximizing Retail And Remote Office Uptime
NodeGrid Serial Console™ is not just for data centers. Retail, Remote Office and POD/POP environments normally do not have dedicated IT support staff available. So who will monitor and repair...
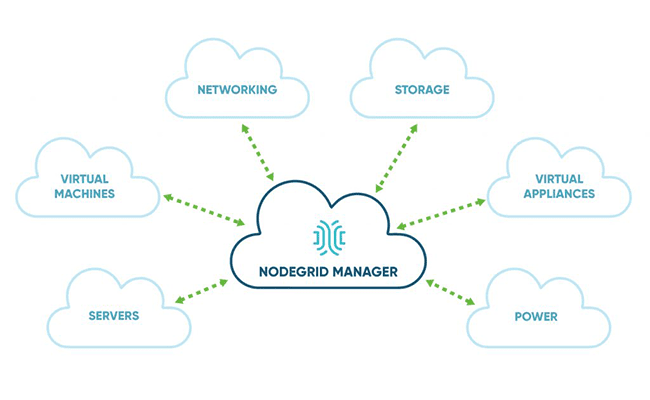
One Easy Way To Consolidate Your Out-Of-Band Management – And Save Money
Did you know there's an easy way to consolidate your Out-Of-Band data center management – and save money? For all that IT provides, there is a constant cry from businessmen to cut costs, find...
Nodegrid 3.0 Generally Available
Nodegrid 3.0 Generally Available FREMONT, CA, September 29, 2015 — ZPE Systems today announced general availability of Nodegrid version 3.0, the core software platform that runs...

It’s Time For a New Set of Tires
When your car needs new tires, or some other repair, (AND YOU KNOW IT) do you wait until you get a flat on the freeway, or break down and need a tow? Or do you (PROACTIVELY) take it to the shop for...

NodeGrid With Monitoring And Dashboard Available
Although we imagine you enjoy getting exercise, we want to make sure that you and your crew don't have to walk around manually resetting servers, virtual machines and routers at the data center or...

Learn About the World’s Fastest Serial Console Switch
What moves faster than bottled water in a desert? The world's fastest, smartest serial console! If you’re planning an upgrade, refresh, or new deployment of serial consoles, there’s never been a...

ZPE Systems Joins the VMware Technology Alliance Partner Program
ZPE Systems Joins the VMware Technology Alliance Partner Program FREMONT, CA, May 5, 2015 — ZPE Systems, Infrastructure Redefined, today announced it has joined the VMware Technology Alliance...

5 Ways to Find Data Center Devices Using NodeGrid Serial Console
How Does Natural Language Search Help Me Find IT Devices in the Data Center? By using NodeGrid Serial Consoles in standalone or cluster configuration, it’s easy to find physical servers, routers and...

Why NodeGrid Serial Console has an x86-64 CPU and More Memory Than Traditional Console Servers
ZPE Systems Recently Released the World's First 64-bit x86 CPU Based Serial Console Server with Faster Processing Speeds and More RAM and Storage Than All Legacy Vendors' Consoles. Hip sysadmins and...

Part 2: Why Build a 96-Port NodeGrid Serial Console?
This is the second of a multi-part series of posts about our new NodeGrid Serial Console product. Why we built it, how we decided on which features to include and why, and more, which we’ll cover in...

Part 1: Our Motivation Behind NodeGrid Serial Console
This is the first part of a serialized exploration of our new NodeGrid Serial Console™ product. Why we built it, how we decided on which features to include and why, and more, which we’ll cover over...

ZPE Systems Unveils NodeGrid Serial Console—96 Port Density, Open Architecture, Intel CPU-based, Fastest Serial Console Server On The Market
SAN JOSE, CA, March 10, 2015 - ZPE Systems® today unveiled NodeGrid Serial Console™. This new generation of serial console switch is the highest density device in the industry and helps data centers...

Free Yourself from Vendor Lock-in!
Back in the early and mid-2000’s the race was on to implement an out-of-band infrastructure (OOBI) to provide access and control to all your IT assets in the data center via a separate management...

The Future of IT Infrastructure Management is Here
You might not know us, but you do. We designed and engineered OOBI appliances that are deployed in the world's largest data centers. We are a group of technologists with more than 100+ years of...
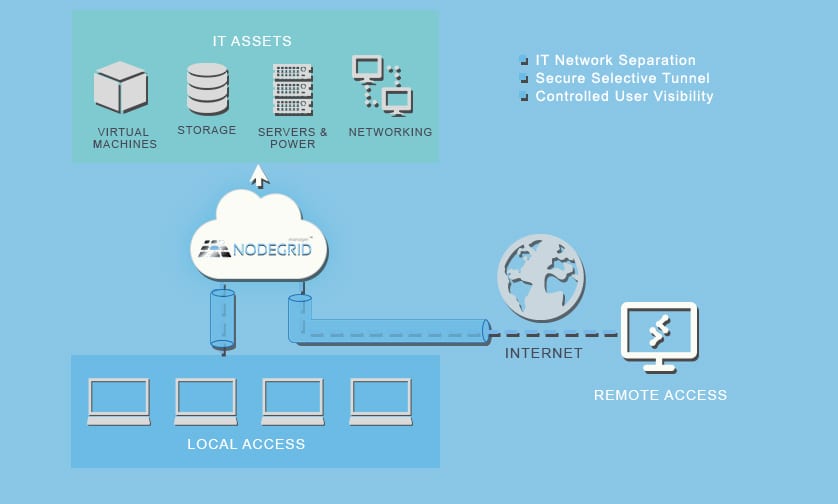
Avoid Future ShellShock Type Attacks
ShellShock UNIX Bash Bug - Introduction You've heard about the ShellShock Unix Bash "ghost user" exploit at least 13 times by now. This discovery of a hurtful secret within a deep, trusted...

Are Your Infrastructure Management Practices Still Valid In Today’s Data Center?
I believe we will all agree that when it comes to technology, “Change is Constant”. Nowhere in the history of time has anything changed as fast as technology over a shorter period. As a byproduct of...
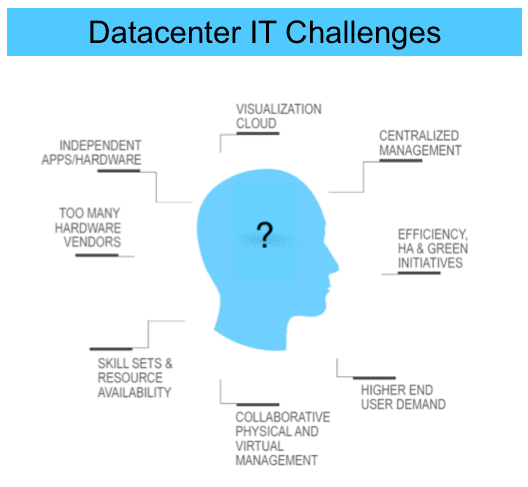
Data Center IT Challenges
I recently came across a survey of 400+ IT Execs and DC Managers regarding the efficiency of their Data Centers, and what they believe would help them make improvements. In general the survey...

Five Reasons To Use Software Defined Access Control
Five reasons to consider Nodegrid Manager ™ for Managing Access to Your Organization's Data Center Assets 1. Nodegrid Manager Makes Life Easy You've got a laundry list of virtual and physical...

Missing Solid Cloud DCIM Access and Control?
Today there are many IT device companies that provide great physical hardware. There are also many good DCIM software tools out there to choose from. But the one piece they’re all missing is a solid...

Data Center Management
Data Center Management: When Challenges become Opportunities We are experiencing a new wave of data center infrastructure challenges. The introduction of virtual network and storage appliances has...
Learn how our Zero Pain Ecosystem can solve your biggest network orchestration pain points.
