How autonomous decommissioning via out-of-band has become essential to disaster recovery for edge deployments in uncertain geographies
To say there’s instability in Eastern Europe would be a drastic understatement. Russia continues its attacks on many fronts in Ukraine, displacing millions of Ukrainians who are now left with an uncertain future. Security is on everyone’s mind, and while many have answered the call to arms and stand ready with AK-74 in hand, others recognize that defending Ukraine involves shielding IT infrastructure and intellectual property from cyberattacks.
For this, some of ZPE Systems’ customers are using an unlikely defense: out-of-band management. Despite recent attacks using wiper malware and DDoS to take down government websites, organizations are able to use generation 3 out-of-band to decommission their sites in order to protect their data against adversaries who have boots on the ground.
In this post, we’ll examine the current issues surrounding compromised edge sites and what organizations are doing right now to shield their intellectual property (IP).
What’s at stake?
Many companies have critical IT infrastructure distributed across countries, regions, and continents. This infrastructure consists of networking gear and edge compute equipment, such as servers, switches, routers, and other end devices. These are responsible for connecting users and customers to essential services, processing and storing sensitive data, and running intellectual property such as proprietary operating systems, applications, and network certificates.
All of these are essential to supporting normal business operations and the customers they serve.
For example, telco companies rely on their infrastructure of cell tower sites, fiber cable lines, and their connected hardware and software to provide voice networks and Internet service. These companies run intellectual property within their infrastructure. In many cases, this intellectual property includes software that can cover a range of types and uses, from multi-protocol access proxies that enable IT admins to remotely manage edge network clusters, to analytics applications that track data usage for media delivery and customer experience optimization.
These companies are also responsible for handling sensitive data. For administrative purposes, billing, and compliance, these companies use devices that process and store personal identifying information for customers, including names, addresses, birth dates, etc.
All of this is what is at stake when faced with disaster. This is why it’s important to have the proper disaster recovery plan and tools in place, and mitigate the risk of losing sensitive information or having it fall into the wrong hands.
What disaster looks like
Every enterprise and government organization should assess their level of risk regarding equipment deployed at the edge. Risks can come from geographical and geopolitical factors — such as tornadoes or flooding during seasons of inclimate weather, or regional instability during times of international conflict.
Imagine you’re in charge of a corporate or government organization. One day you stop receiving pingbacks from your edge sites, and you suddenly find that you’re cut off from these locations.
There’s no network. There’s no access. And like many organizations currently struggling in Ukraine, you’re simply no longer in control of what happens to your data.
What do you do now?
Your sensitive user credentials, customer information, and intellectual property are in jeopardy, and possibly being stolen by adversaries.
Could you have prevented this?
Disaster recovery: Autonomous decommissioning to stop data theft
Part of an adequate disaster recovery plan involves having hermetic and autonomous operations, down to the device level. In the case that you need to go into disaster recovery mode, consider all of the information that needs to be wiped at your locations:
- Servers need to be wiped
- Disks and partitions need to be wiped
- Disks need to be overwritten so data can’t be recovered
- Switches and supporting infrastructure need their configurations wiped
The problem is that since you’re cut off and unable to remotely access this equipment, you can’t perform these tasks.
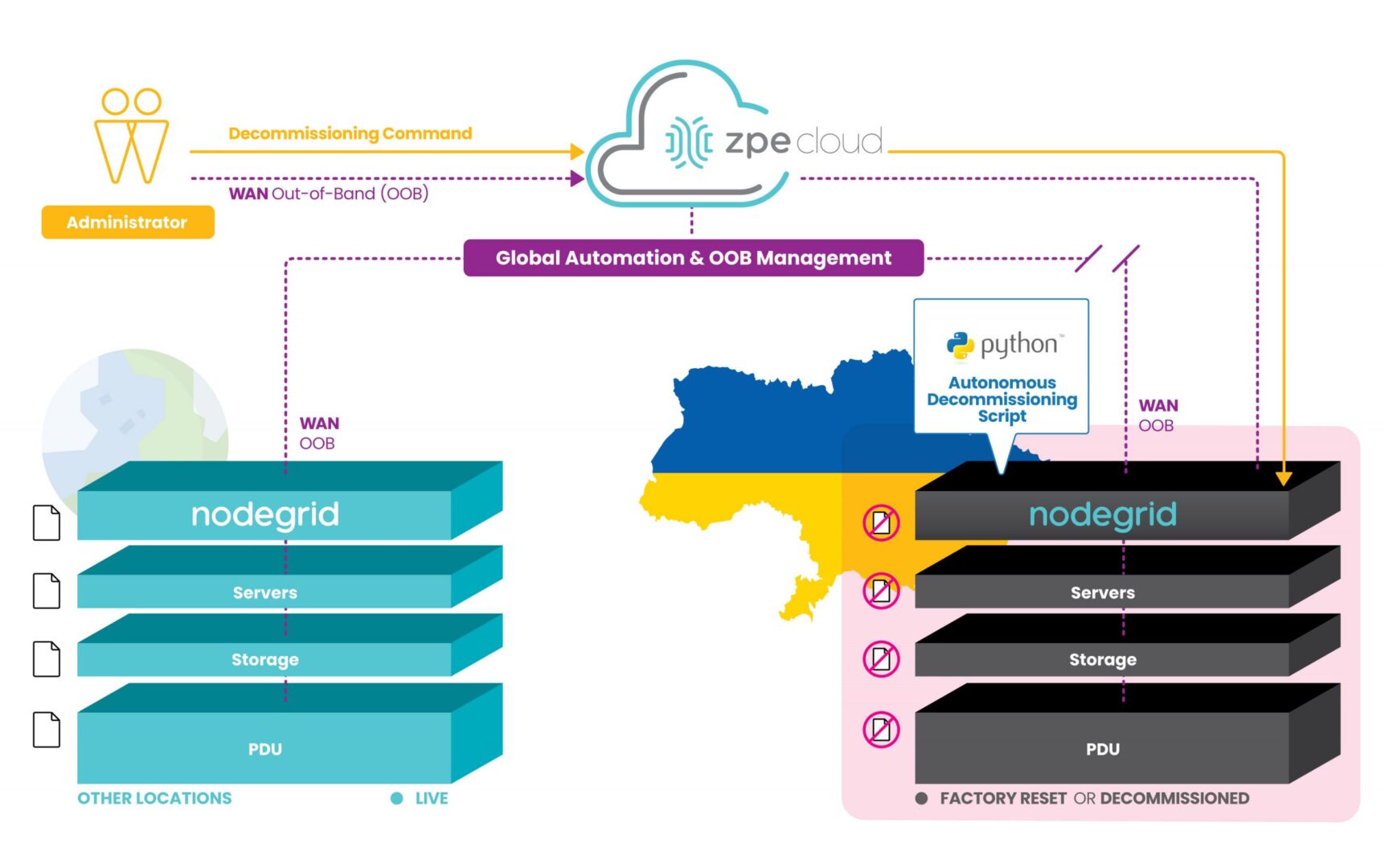
However, ZPE’s customers are currently using our programmable out-of-band infrastructure for this exact use case. It’s being called ‘autonomous decommissioning’, and it combines network automation with manual commands to essentially perform the inverse of launching network sites. This process is being used to protect IP and personal identifying information from falling into the wrong hands.
How does it work?
With our generation 3 serial consoles and services routers co-located at data center and critical edge locations, customers are able to connect all of their equipment to the out-of-band network. Receiving pingbacks at regular intervals from HQ signals that all is well at these sites.
Due to instability in the region, some sites are becoming compromised and cut off from HQ. When this happens, the infrastructure goes into disaster decommissioning mode, and ZPE’s devices serve as on-prem automation workers which help remote IT admins to begin wiping the entire infrastructure.
These devices are hooked into every piece of equipment, and they’re able to receive automated scripts and manual commands from remote admins to push decommissioning tasks to all connected gear. The ZPE device is then able to have its own configuration wiped and returns to its initial ‘seed of life’ mode, in which it awaits further instructions until the connection is restored to HQ. Once this connection is restored, Nodegrid waits for instructions to rebuild the infrastructure following the immutable infrastructure framework.
This autonomous decommissioning prevents data from being stolen by adversaries. By wiping all data and returning to its seed-of-life state, it also keeps the environment’s configurations secure. That’s because the devices no longer contain any configuration information once they’ve been wiped, and configurations can only be restored once an authenticated connection is reestablished with HQ.
Check out a live demo at ONUG!
See how to automate without anxiety to combat cyberattacks. Join us Thursday, April 28 at 11:10am EST at ONUG for a live demo. Click here to register or get your free virtual pass.